Compliance
Continuously Uphold Regulatory and In-House Standards.
Myrror ensures your compliance by continuously scanning for both known and emerging threats across your supply chain, helping you meet the highest industry standards.
The Growing Complexity of Compliance
Modern organizations are required to meet strict security standards, such as SOC2, NIST, ISO27001, and more. With new requirements emerging each year, Myrror automates security scans across both 1st- and 3rd-party code, while also generating compliant SBOMs for your entire codebase.
Comprehensive Coverage
Myrror helps your organization comply with all standards that require static scanning of your code and the generation of software inventories, including SOC2, ISO270001, and PCI.
Automated Auditing
Myrror runs continuous, daily audits that include every changes your codebase goes through to ensure you remain compliant over time.
SBOM Generation
Myrror offers completely automated software bill of materials (SBOM) generation to satisfy executive order 14028.
Software Supply Chain Attack Detection
Remediation Plan Generator
SBOM & Binary SBOM
Reachability SCA
SAST
Utilizes The Best Myrror Has to Offer
We leverage our SAST, reachability-based SCA, and SBOM generation capabilities to address your compliance needs. SAST secures your code from the start, while our SCA provides deep insights into third-party dependencies, and our SBOM generator ensures you meet regulatory reporting requirements.

How It Works
Step 1
Scan 1st-Party Code with our SAST - Detect vulnerabilities, coding errors, and security flaws early in the development process, enabling developers to address issues before they escalate into significant risks.
Step 2
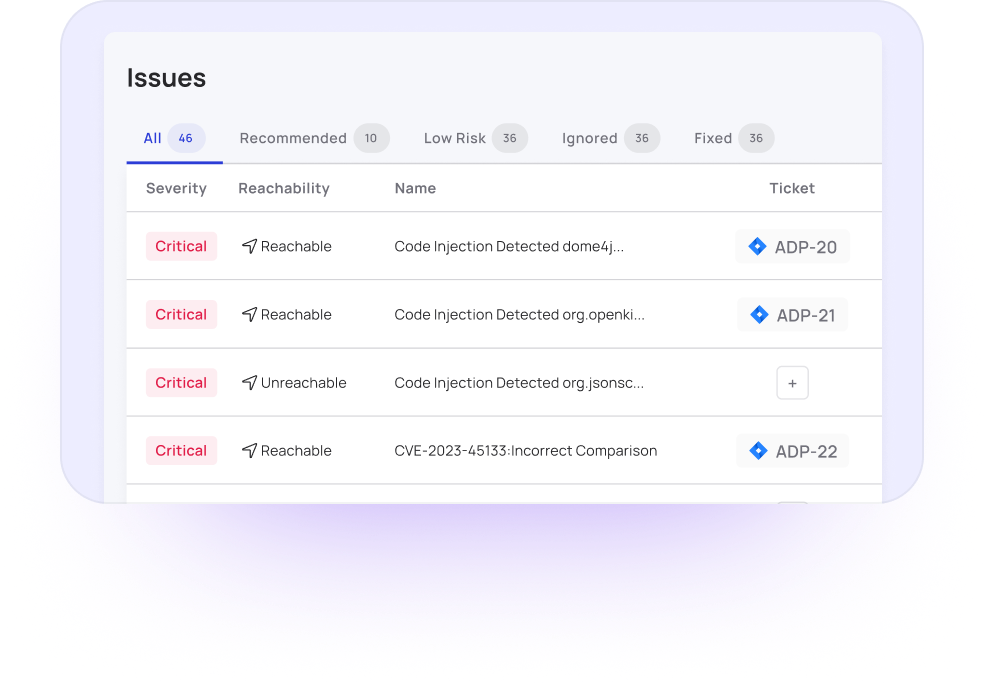
Detect Vulnerabilities & Supply Chain Attacks in 3rd-Party Code with Our SCA — Myrror identifies vulnerabilities and supply chain threats, prioritizing them based on the context of your application and reducing up to 80% of the noise.
Step 3
Generate SBOM Reports - Automatically generate and export Software Bill of Materials (SBOM) reports for both source code and binaries (coming soon!) to meet the requirements of Executive Order 14028 and other standards.
Myrror For Compliance
Myrror helps you meet various compliance standards, automating audits and ensuring regulatory reporting across your workflows.
SAST Insights
Detect vulnerabilities early in your development process by scanning for compliance-related issues in your code.
Myrror’s SAST provides detailed reports, showing where your code fails to meet various industry standards like SOC2 and ISO27001, and prepares a detailed remediation plan (see below).
SCA Reporting
Stay ahead of compliance risks in your third-party and open-source components with detailed insights into known vulnerabilities, and protect yourself from supply chain attacks in the process.
Myrror enriches CVE data from the NVD database by factoring in reachability, exploitability, available fixes, and the perceived maliciousness of new code being introduced.
SBOM Generation
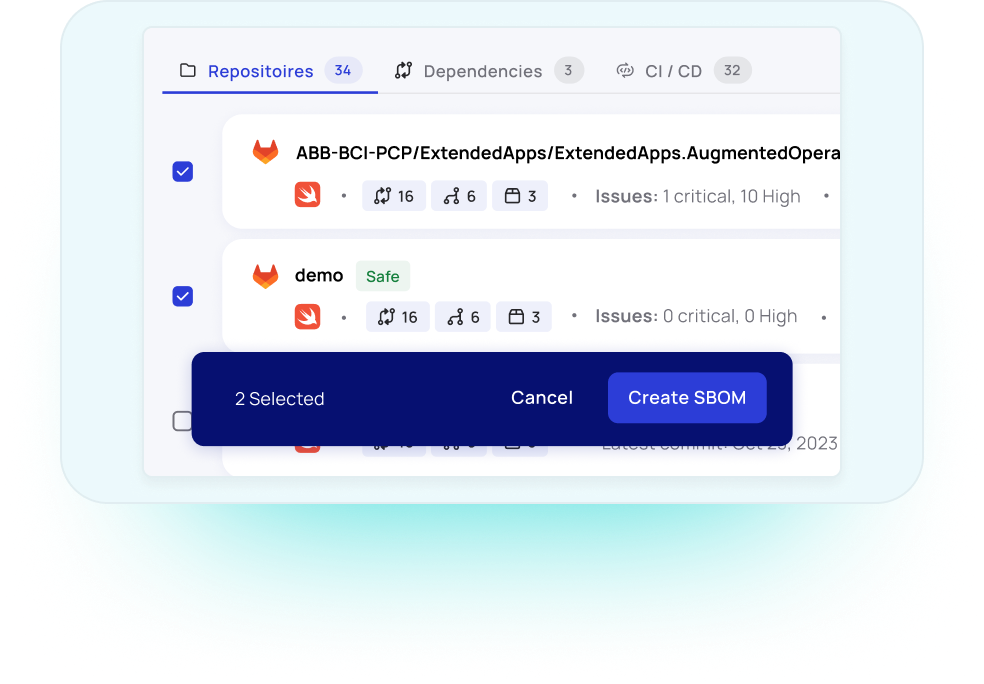
Myrror automatically generates SBOMs for individual, grouped, or all of your repositories in the industry-standard CycloneDX format.
It continuously tracks every component in your codebase, ensuring you’re always ready to meet even the most demanding software inventory requirements.