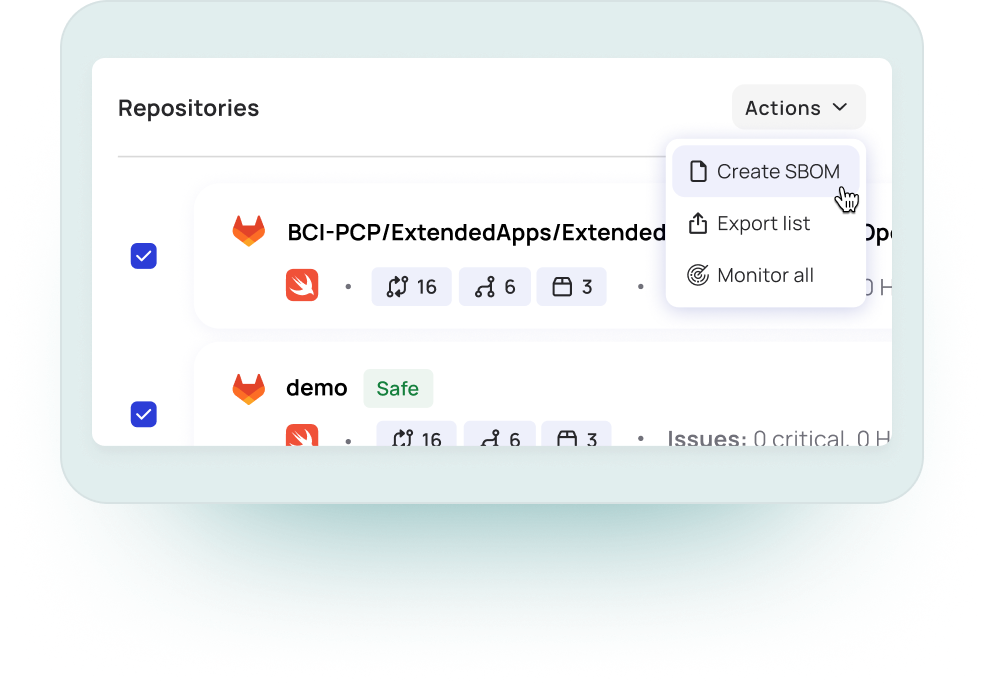
SBOM & Binary SBOM
Tally Up Every Incoming (Or Outgoing) Piece of Code.
Myrror’s SBOM allows you to easily import 3rd party SBOMs, and export your own SBOMs from binaries, repositories, and CycloneDX/SPDX files.
What are SBOMs & Binary SBOMs?
Myrror’s Software Bill of Materials (SBOM) catalogs all components of your software, provides insight into potential risks within open-source dependencies, and incorporates VEX exploitability information into the final result. We go even further by generating a Binary SBOM that documents the binaries within your dependencies, ensuring complete visibility—even for compiled code.

In Practice:
Step 1
Myrror automatically detects and catalogs all components within your codebase, ensuring full visibility of dependencies.
Step 2
Myrror scans binaries from third-party libraries to identify any hidden vulnerabilities and detect malicious code patterns within previously-compiled code.
Step 3
Myrror generates industry-compliant SBOM reports in popular indu formats, including SPDX and CycloneDX.
Key Features of Myrror’s SBOM Generator
Myrror’s SBOM & Binary SBOM tools offer deep insights into your software’s components. By documenting both source code and binaries, you gain comprehensive coverage of your third-party dependencies, ensuring no potential risks go unnoticed.
Automatic SBOM Generation
Myrror automatically generates CycloneDX SBOMs for single repositories, groups of repositories or your entire codebase.
This ensures that your organization is continiously compliant with regulations like Executive Order 14028 and SOC 2 Type II.
Binary SBOM
Myrror digs deeper by creating Binary SBOMs, documenting the binaries in your third-party dependencies. This helps you uncover hidden risks in compiled code, which often goes unnoticed in traditional scanning methods.
With this feature, your team can address vulnerabilities even in binaries where source code may not be available.
See How We Do It
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam