Vulnerability Prioritization
An End to Endless Vulnerability Alerts
Myrror prioritizes your vulnerabilities not only based on their presence in the code but also considering their reachability and exploitability. Gain true visibility into the vulnerabilities that matter most and put an end to alert fatigue.
Too Many Vulnerabilities, Too Little Time
Application security teams spend 30-50% of their time triaging vulnerabilities, often lacking context to prioritize what truly matters.
Myrror’s SCA cuts through the noise, enabling teams to focus on the most urgent risks using deduplication, reachability analysis, and contextual prioritization.
Focus on Urgent Risks
Prioritize the most critical vulnerabilities and supply chain attacks based on reachability and actual business impact.
Deduplicate Similar Issues
Myrror deduplicates issues that arise from the same source across multiple repositories automatically, saving on time and developer effort.
Actionable Context
Myrror enriches each alert with a highly-granular information that’s needed to prioritize what truly matters.
Software Supply Chain Attack Detection
Remediation Plan Generator
SBOM & Binary SBOM
Reachability SCA
SAST
Utilizes The Best Myrror Has to Offer
Myrror’s SCA identifies exploitable vulnerabilities, reduces triaging time by deduplicating issues, and prioritizes risks based on their reachability and potential impact on production environments.

How It Works
Step 1
Myrror connects to your SCM and automatically begins a discovery process, mapping all the dependencies across your repositories.
Step 2
Myrror scans for known security risks and supply chain attack attempts in real time, for both CVE-bearing vulnerabilities and supply chain attacks that have no known CVE number.
Step 3
Myrror’s determines if the vulnerability is actively reachable and if an exploit is circulating in the wild, offering prioritized risks with fixes where available.
Key Features of Myrror’s Vulnerability Prioritization
Myrror’s SCA approach centers on reachability, while also evaluating the exploitability of each vulnerability. In addition, the platform enables a developer-first remediation process, allowing teams to prioritize critical risks, minimize noise, and streamline their remediation efforts.
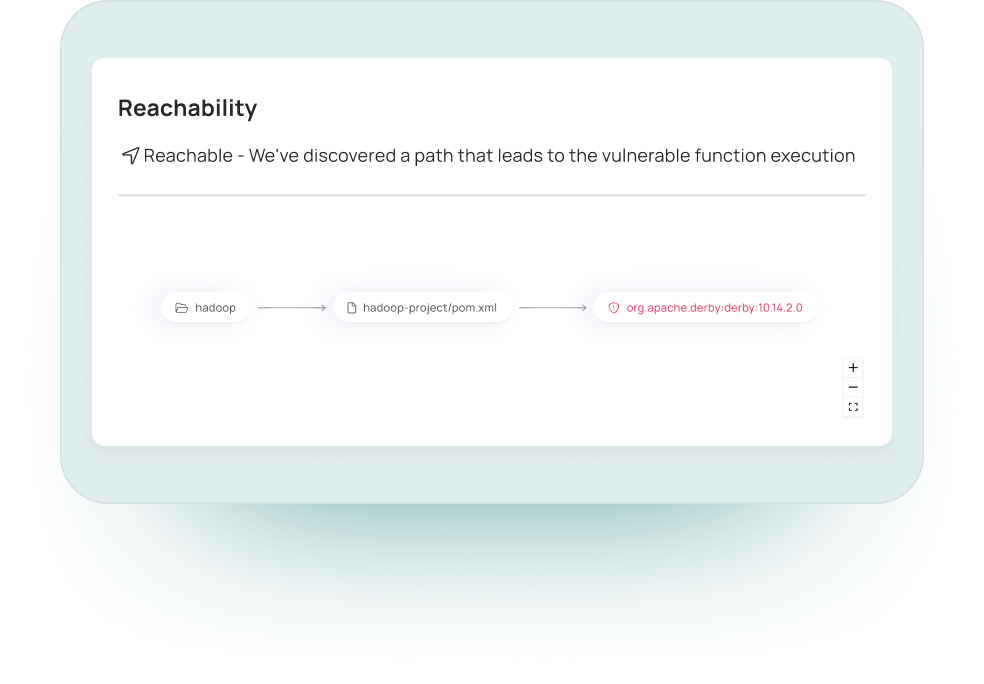
Reachability
Traditional SCAs read the manifest file, see if a vulnerable version of the package exists, and mark the vulnerability as a risk.
Myrror’s Reachability Engine analyzes both direct and indirect dependencies, and concentrates on determining if a specific piece of vulnerable code is reachable, and only flags packages that can be reached in practice.
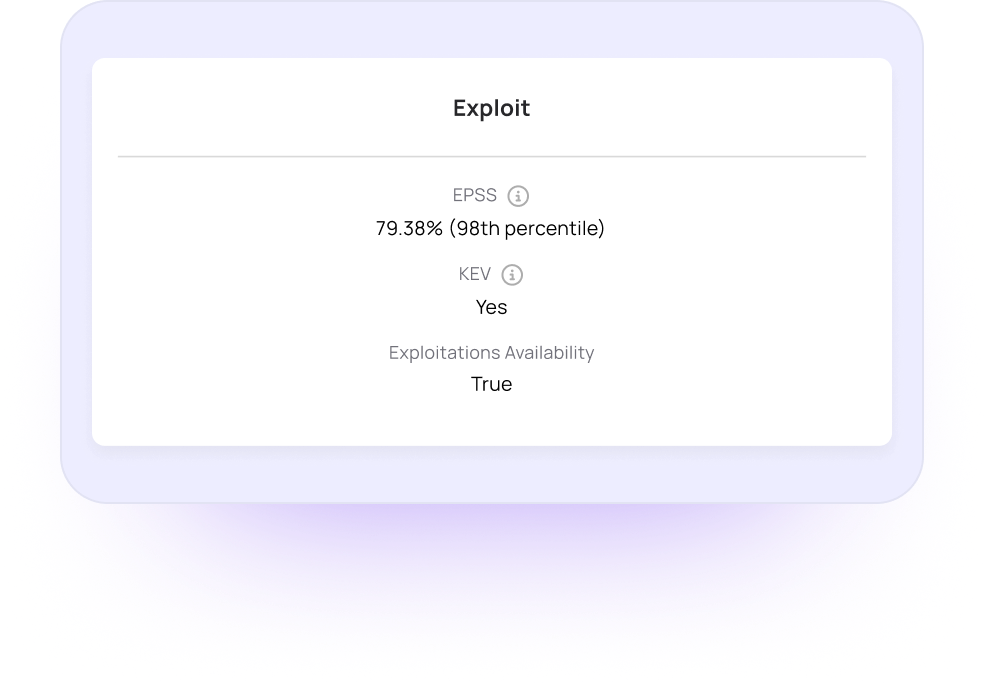
Exploitability Analysis
Reachability indicates that the vulnerable code can be accessed in practice, but this does not necessarily imply it can be exploited.
Myrror enriches the findings with multiple exploitability data sources and marks each vulnerability with a flag to indicate whether an exploit for it is actually available – allowing for even deeper prioritization.
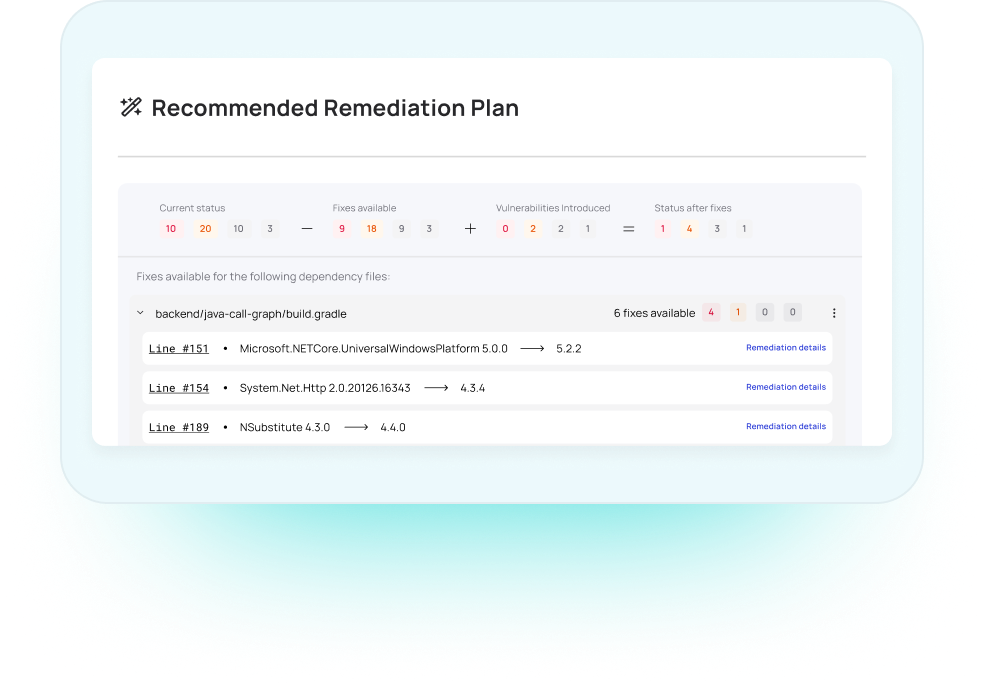
Contextual Remediation
Myrror’s remediation planner focuses on generating a detailed game plan out of the risk prioritization our Reachability SCA creates.
To do so, we dive deep into the context of your application and provide a set of line-by-line steps your engineering team can take to remediate each risk, estimate the amount of effort each fix will require – then bundle up tasks in clear & concise todo lists custom-made for developers.