Supply Chain Attacks
Stomp Out Next Generation Open Source Risks
Binary-To-Source AI Engine (Patent Pending) detects malicious and compromised open-source packages, typosquatting, dependency confusion, CI/CD attacks and more without any CVE to identify them.
What is Supply Chain Attack Detection?
Supply chain attacks exploit flaws in third-party software components your company uses, via undisclosed vulnerabilities. Myrror’s detection system automatically identifies any suspicious code or behaviors introduced through external dependencies, preventing your organization from being compromised by malicious actors.

In Practice:
Step 1
Myrror scans all third-party dependencies and CI/CD builds, monitoring for unusual behavior or unverified sources, and identifies sophisticated software supply chain attacks, including Solarwinds, 3CX, and XZ-Utils.
Step 2
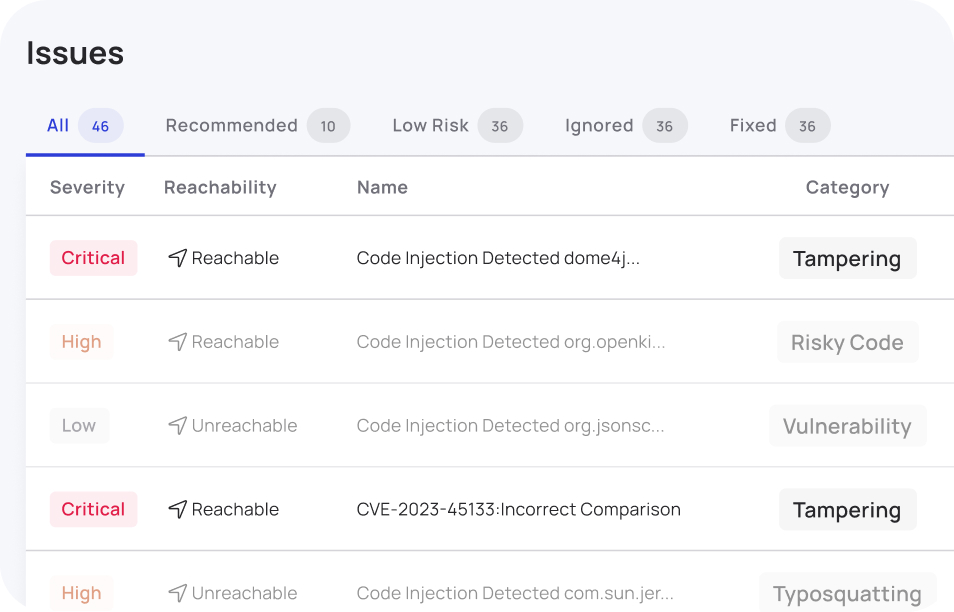
Myrror identifies malicious code, binaries, tampering code injection and more and flags them as risks, checks their reachability and exploitability, and uses proprietary AI techniques to assess the maliciousness of each abnormality.
Step 3
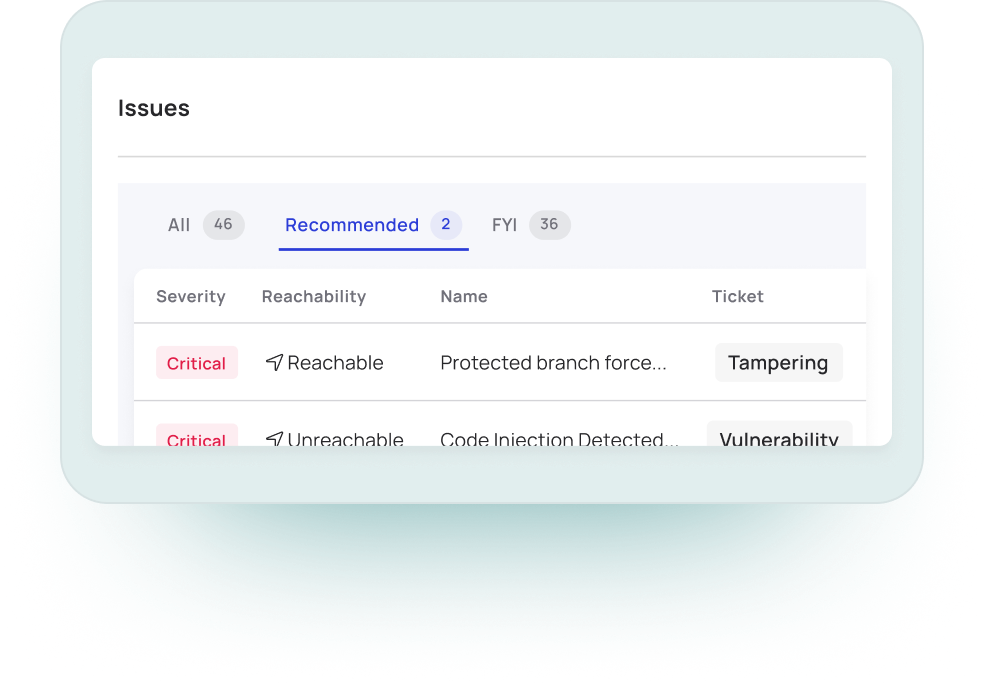
Myrror pushes supply chain attacks to the top of the backlog, and immediately alerts on any potential or ongoing attack even as the situation is unfolding.
Key Features of Myrror’s Supply Chain Attack Detection
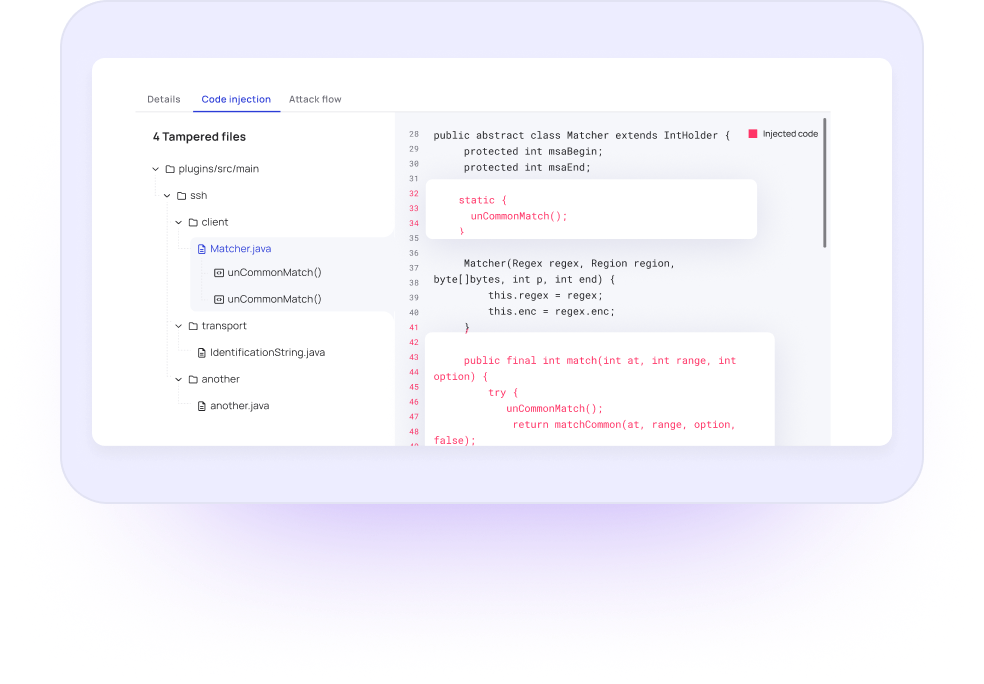
Myrror’s Integrity Engine uses binary-to-source analysis techniques to detect whether the dependency you’re using is in fact that dependency you expected, and protects against various forms of supply chain attacks like typosquatting, code injection, maintainer compromise and more.
Attacks VS. Vulnerabilities
Traditional SCAs protect against known vulnerabilities, while Myrror also detects supply chain attacks, which:
- Is a deliberate malicious activity, unlike a vulnerability, which is more often than not unintentional and the result of a non-deliberate mistake
- Lacks specific CVE identification
- Are untracked by standard SCAs and public databases
- Typically, it has already been attempted to be exploited by the time you discover it
Integrity Engine
Reachability indicates that the vulnerable code can be accessed in practice, but this does not necessarily imply it can be exploited.
Myrror’s proprietary analysis engine assesses whether the vulnerable code is actually exploitable and marks each vulnerability with a flag to indicate whether an exploit for it is actually available – allowing for even deeper prioritization.
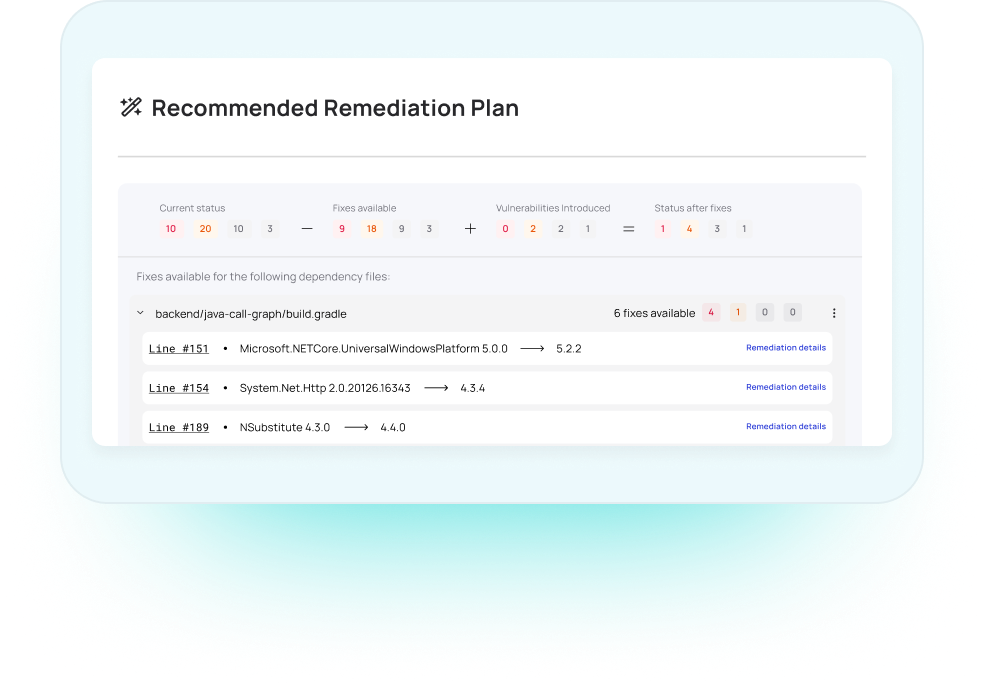
Attack Remediation Advice
Myrror goes beyond detection by offering detailed, concrete fix plans for supply chain attacks.
When a threat is identified, the platform generates actionable remediation steps, helping teams resolve vulnerabilities quickly and efficiently. This includes patching vulnerable dependencies, removing malicious code, and deploying safe alternatives if such exist.
See How We Do It
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam