As each year goes by, the world demands more from software applications. To meet this demand, data generation is skyrocketing. According to IDC, global data creation is projected to reach 221 zettabytes by 2026, driven by the explosion of connected devices, AI-powered systems, and cloud-first development practices.
To keep up with this demand, companies continue to invest heavily in cloud-native application development. In fact, global public cloud spending is projected to exceed $679 billion in 2025, reflecting the increasing reliance on cloud platforms to accelerate innovation and scalability. This strategy enables development teams to leverage modern tools and architectures to build, deploy, and manage applications entirely in the cloud. While this speeds up delivery cycles, it also introduces new security risks that must be carefully managed.
This guide explains why cloud application security matters, the biggest vulnerabilities and threats, and best practices to consider for great cloud application security.
Why Does Cloud Application Security Matter?
When building cloud applications, you’ll store large amounts of private data on cloud providers. Cybersecurity Ventures predicts that by 2025, cyber-attacks will cost businesses over $10.5 trillion annually. They also estimate that 90% of these attacks will be due to cloud security vulnerabilities.
To combat this problem, companies must step up their game and implement robust cloud application security measures by prioritizing security across the SDLC and their operations. Cloud security tools can help, including:
- Cloud workflow protection platform (CWPP)
- Cloud access security broker (CASB)
- Cloud infrastructure entitlement management (CIEM), etc
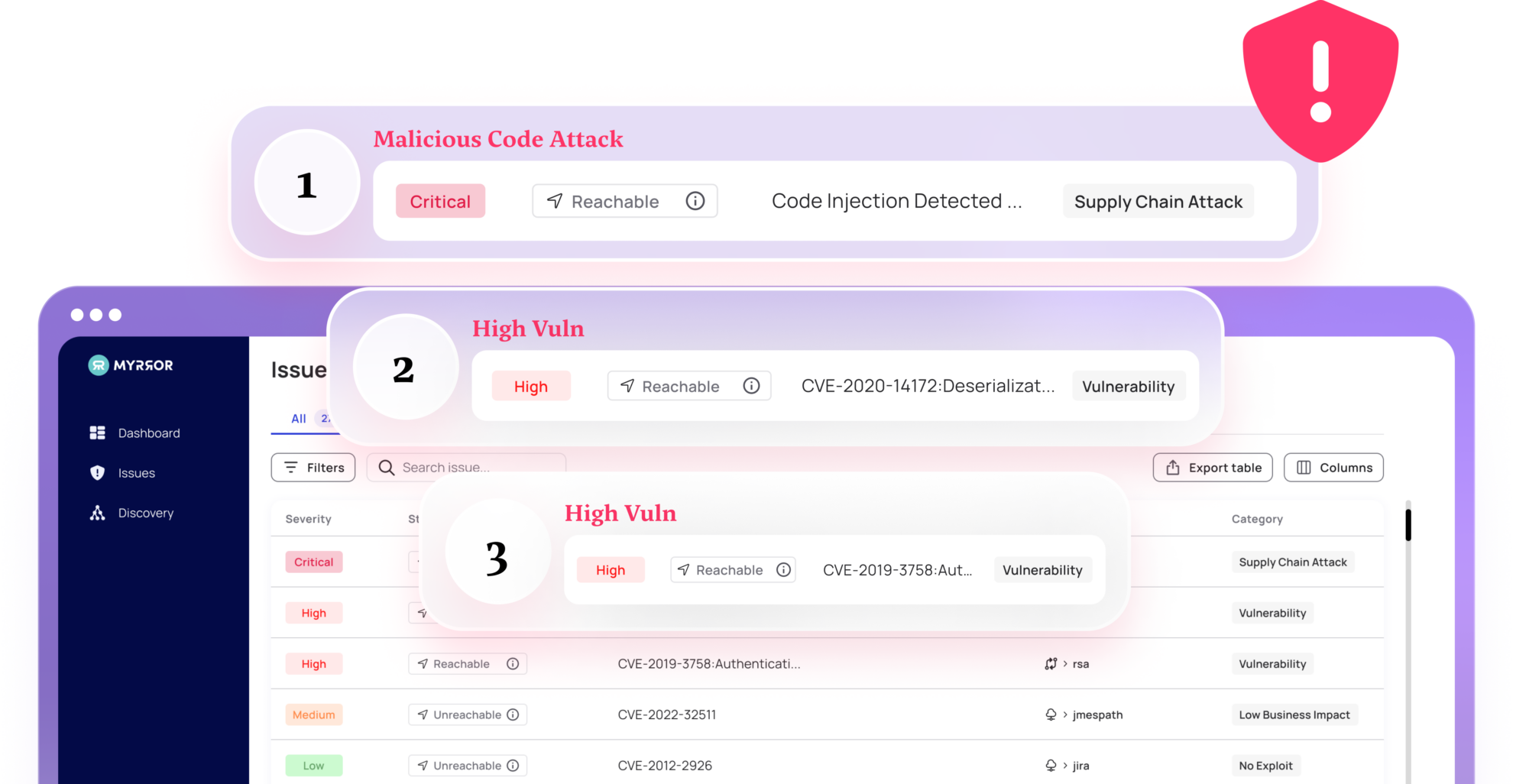
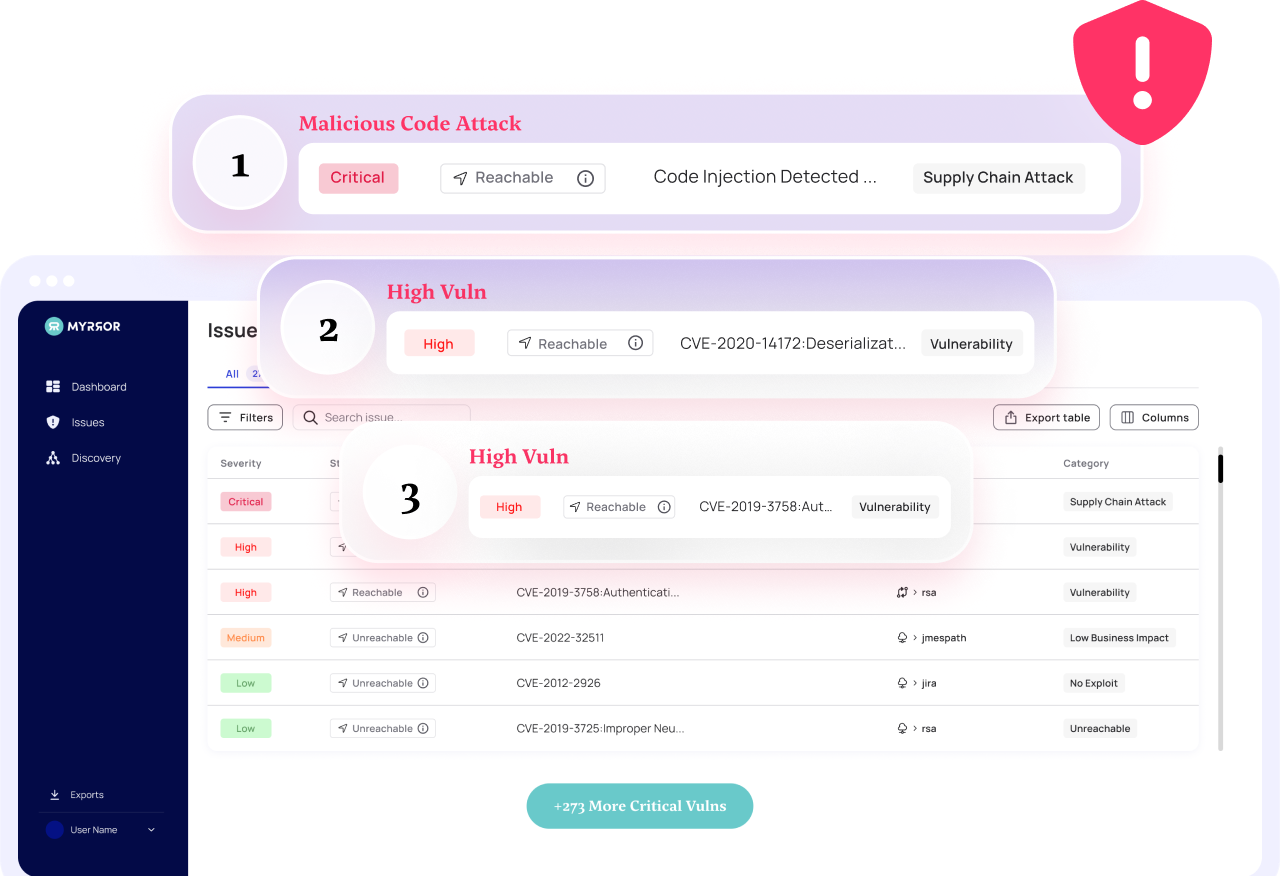
What are the Biggest Cloud Application Security Vulnerabilities and Threats?
Cloud application security vulnerabilities and threats continue to impact some of the world’s most recognizable names in tech. In recent years, companies like Microsoft, Okta, MGM Resorts, and 3CX have all disclosed significant cybersecurity incidents—many of which involved third-party integrations, misconfigurations, or social engineering. Below, we’ve outlined some of the most prominent vulnerabilities that have emerged across the tech landscape and could just as easily affect your organization.
Misconfiguration
Over 90% of companies use some Infrastructure-as-Code (IaC), but 50% are managing at least fifty cloud misconfigurations every single day. When developers write open source boilerplate templates and blog posts, most forget to review them in line with cloud application security best practices, hence why misconfigurations happen at this scale.
Lack of visibility
With the rapid shift to the cloud, companies lose much-needed visibility over their applications due to the complexity of configuration management and insufficient monitoring and observability across cloud service providers.
A lack of visibility creates potential attack vectors because redundant cloud resources that require manual deletion may be hidden, plus your application’s dependencies will go out of date or become vulnerable. Aside from the potential threats, the financial cost of breaches can be high.
Phishing and social engineering
Social engineering attacks are becoming more frequent and more damaging. In 2023, MGM Resorts suffered a high-profile breach after attackers tricked an employee through a help desk phone scam, ultimately leading to ransomware deployment, service outages, and losses exceeding $100 million. This incident highlights how attackers increasingly rely on manipulating human behavior—not just exploiting technical flaws—to infiltrate even the most well-resourced organizations.
6 Best Practices for Great Cloud Application Security
There are a lot of ways in which attackers can breach your cloud security, but following the right security practices can make it harder for them to access your data and exploit vulnerabilities. To ensure you’ve done everything you can, you should cover all the bases, including:
1. Protect Data Before it Reaches the Cloud
One common mistake companies make is assuming that a cloud service provider guarantees data security. In reality, most cloud service providers operate under a shared responsibility model, leaving customers with the task of securing and managing their application data on the cloud. To protect your sensitive data before it reaches the cloud, take the following steps:
- Encrypt the data transfer channel: You can do this by implementing secure protocols such as HTTPS and TLS.
- Encrypt the sensitive data: Even if attackers compromise the transfer channel of the data, they wouldn’t be able to read the actual data.
- Encrypt the data at rest: Encrypting the data storage mechanisms with robust encryption algorithms such as AES-256 can give your application the highest level of encryption without compromising performance.
- Set least-privilege access to the data: Restricting access using methods like role-based access control (RBAC) will decrease the risk of breaches and data leakage.
2. Increase Your Use of IAM (Identity and Access Management)
IAM plays a vital role in maintaining cloud application security, but unfortunately, companies don’t fully utilize its capabilities. With the right IAM strategy, companies can authenticate and authorize employees by providing user-specific access to cloud resources. To increase your IAM usage, consider implementing some of these leading IAM practices:
- Avoid using root accounts: Avoid sharing your root credentials with anyone. Instead, create unique IAM users with the necessary permissions.
- Limit privileged accounts: For each IAM user you create, be sure you give them the least amount of permissions needed for their job.
- Monitor everything: Employ a zero-trust policy and constantly monitor and secure your users’ identity and access points. This will help you detect suspicious activities, such as sign-in attempts from multiple locations, and send alerts to mitigate threats.
- Perform regular audits: Audit user credentials regularly and monitor the lifecycle of passwords and access keys.
3. Create a Strategy for Human Error
If the Twitter social engineering hack taught us anything, it’s that your systems are still prone to human error no matter how technically secure your systems are. According to Tripwire, 35% of companies say their staff have low security awareness, and 39% say they lack skilled employees to protect against cyber attacks.
That’s why it’s becoming increasingly important to train personnel to become human firewalls, which might include changing hiring practices or expanding the search radius to attract knowledgeable team members.
4. Secure Increasing Deployment Velocity
One of the biggest benefits of the cloud is that it enables faster product development. However, the risk is that rushed deployment leads to bad code, half-hearted security processes, and security drift, which has a domino effect and increases the risk of breaches, poor performance, and compliance issues. To manage this, consider using automated security tools that:
- Enable continuous monitoring and regular audits
- Help establish operational baselines and benchmarks
- Automate repetitive security tasks to reduce human error
5. Automate Your Cloud Security Monitoring
Automating cloud security monitoring enables you to detect and remediate risks to ensure your SDLC doesn’t drift from its secure state. When automating your cloud security monitoring, it’s important to add your security protocols in the CI/CD cycle as soon as possible to reduce the likelihood of misconfigurations and ensure continuous testing throughout the development phase.
6. Shift More Left
Security testing used to occur at the end of the SDLC, but it is happening earlier than ever. By taking a shift-left approach and leveraging tools that automatically detect vulnerabilities early in development, teams can remediate risks as code is created. This eliminates the need to waste time recalling old codes and fixing risks late in the production stage.
Make Security Your Priority
Now that you understand the best practices for cloud application security, the next challenge is implementation. As development velocity increases, it’s easy for security to become an afterthought—but it doesn’t have to be.
By embedding security throughout your SDLC—from design to deployment—you can reduce the risk of breaches, ensure compliance, and maintain the trust of your users. Invest in tools and processes that enable automation, early detection, and continuous monitoring to stay secure as you scale.