<span data-metadata=""><span data-buffer="">Remediation-first
Application Security
Myrror is the only AppSec solution that protects you against the most destructive, supply chain attacks, determines the reachability of known vulnerabilities, and provides a contextualized fix plan– with or without a CVE.


Trusted by Leading Security Teams at:
False Positives & Triaging are Wasting Your Time

Malware Blindness
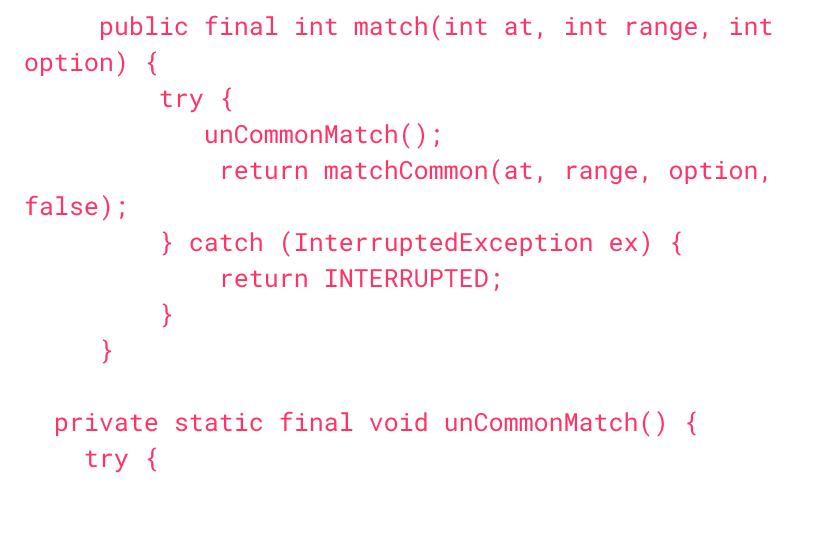
Existing scanners scan for vulnerabilities only, missing malicious packages and malware.

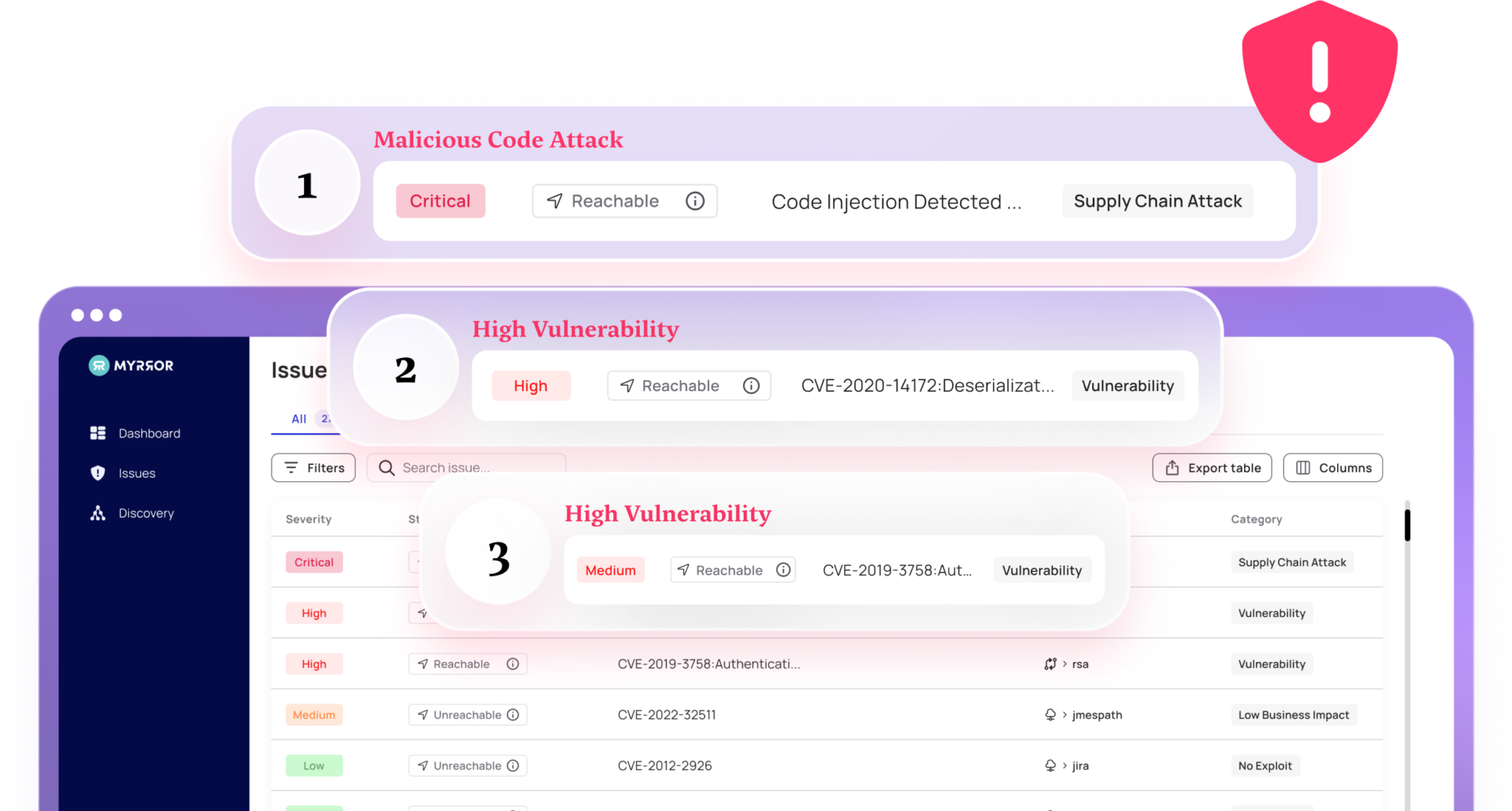
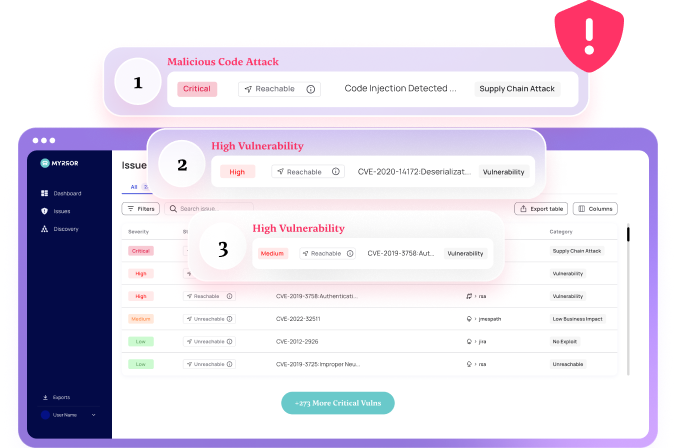
Alert Fatigue
Irrelevant and non-actionable alerts your tools generate lack context and proof of usage in your application.

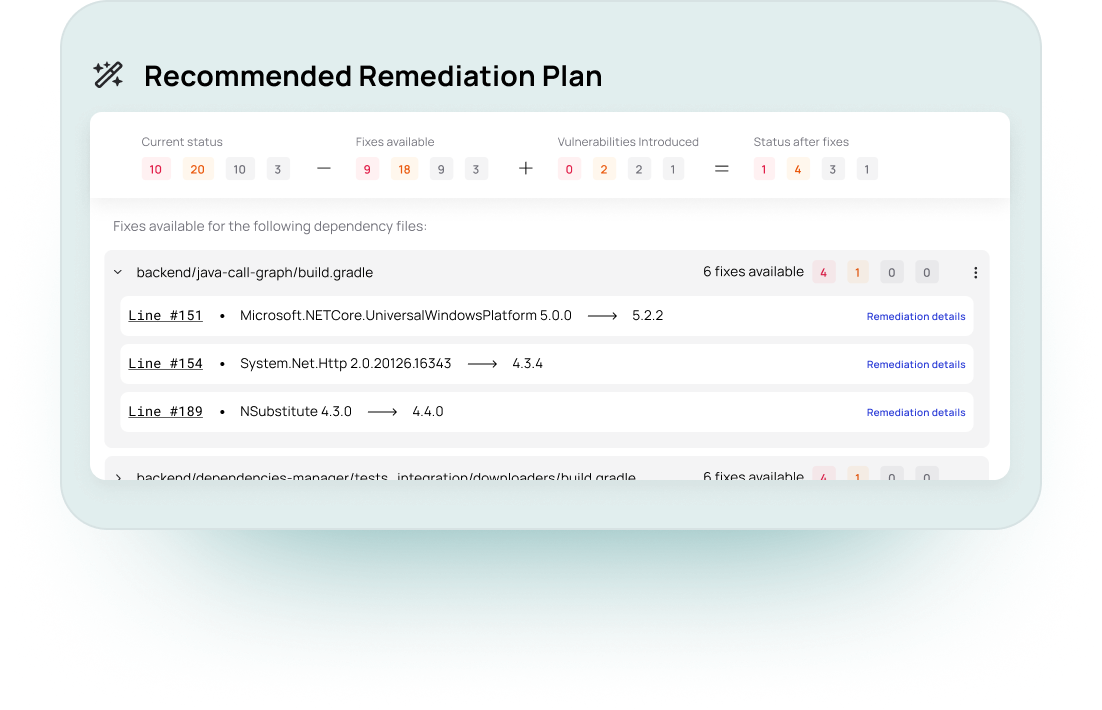
Remediation Guesswork
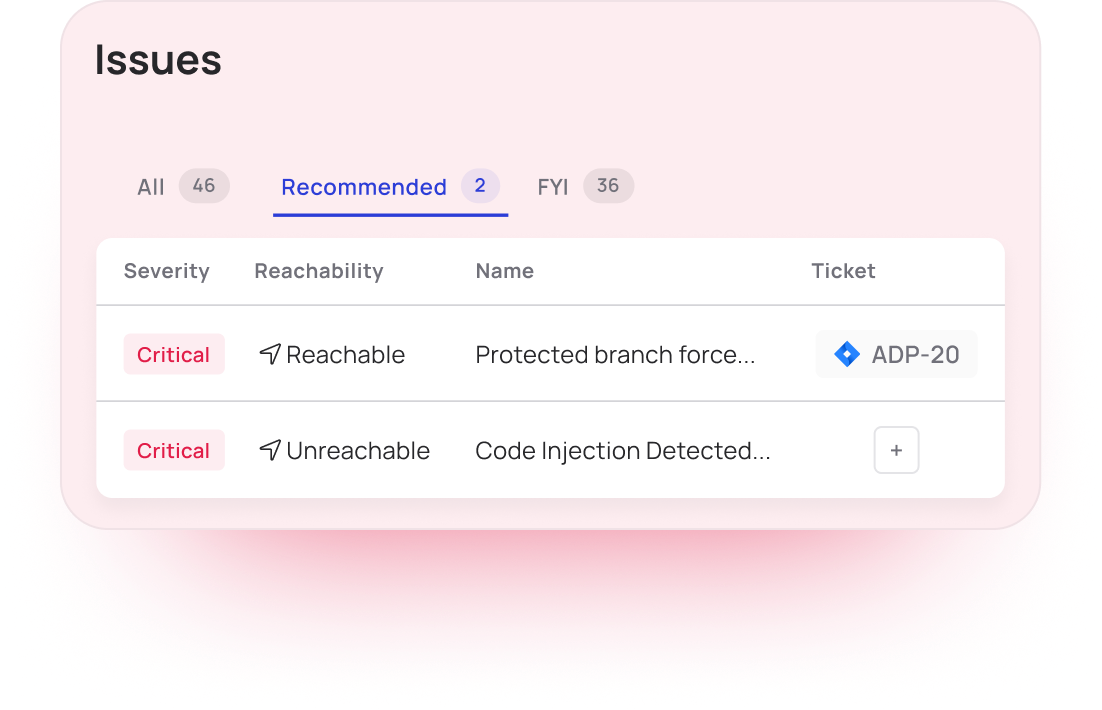
Remediation that lacks prioritization and context wastes security and engineering time.
Prioritize & Fix Risks Based on Application Context
Myrror In A Nutshell
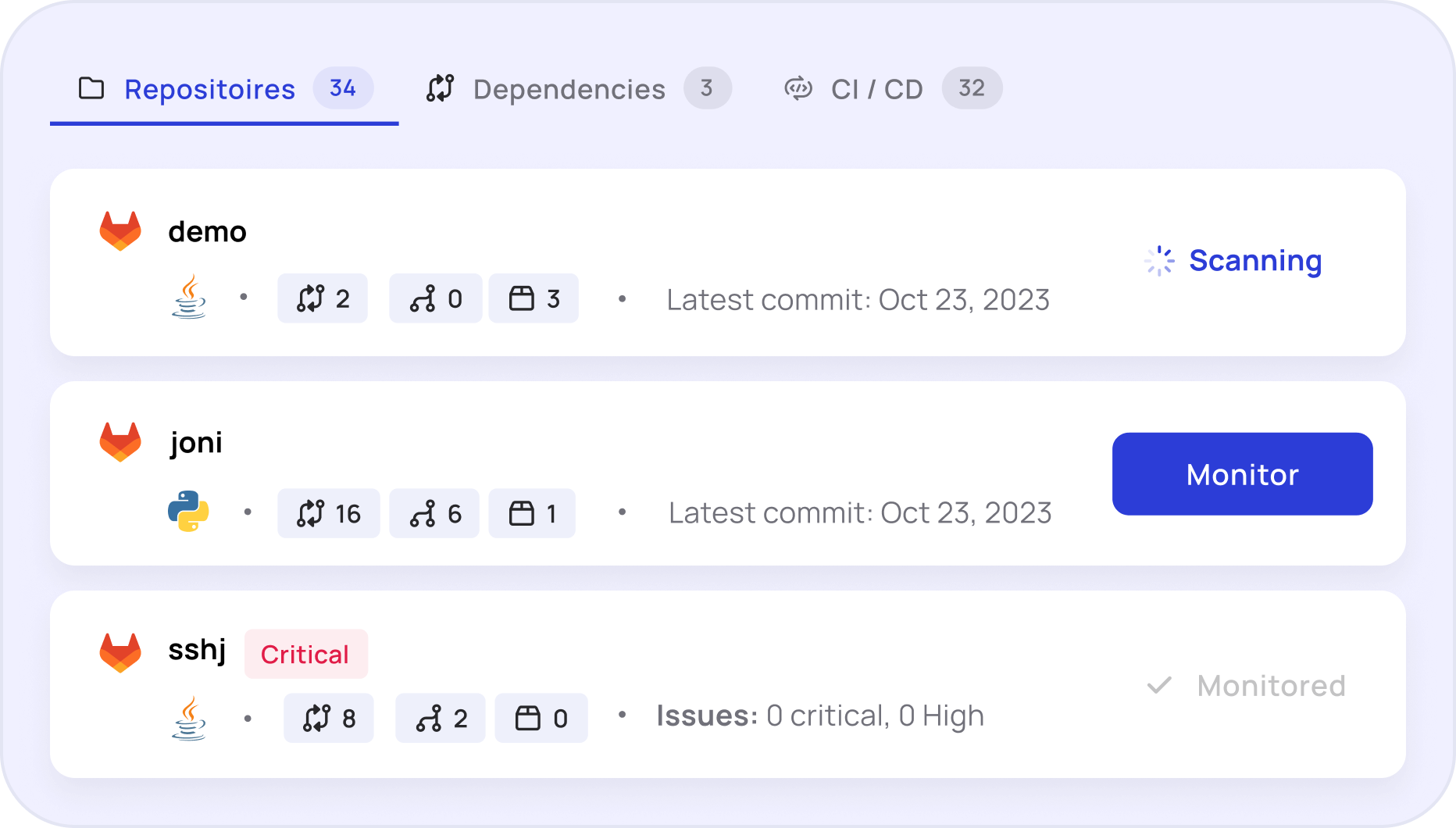
Analyze Every Asset
Triage Vulnerabilities Effectively
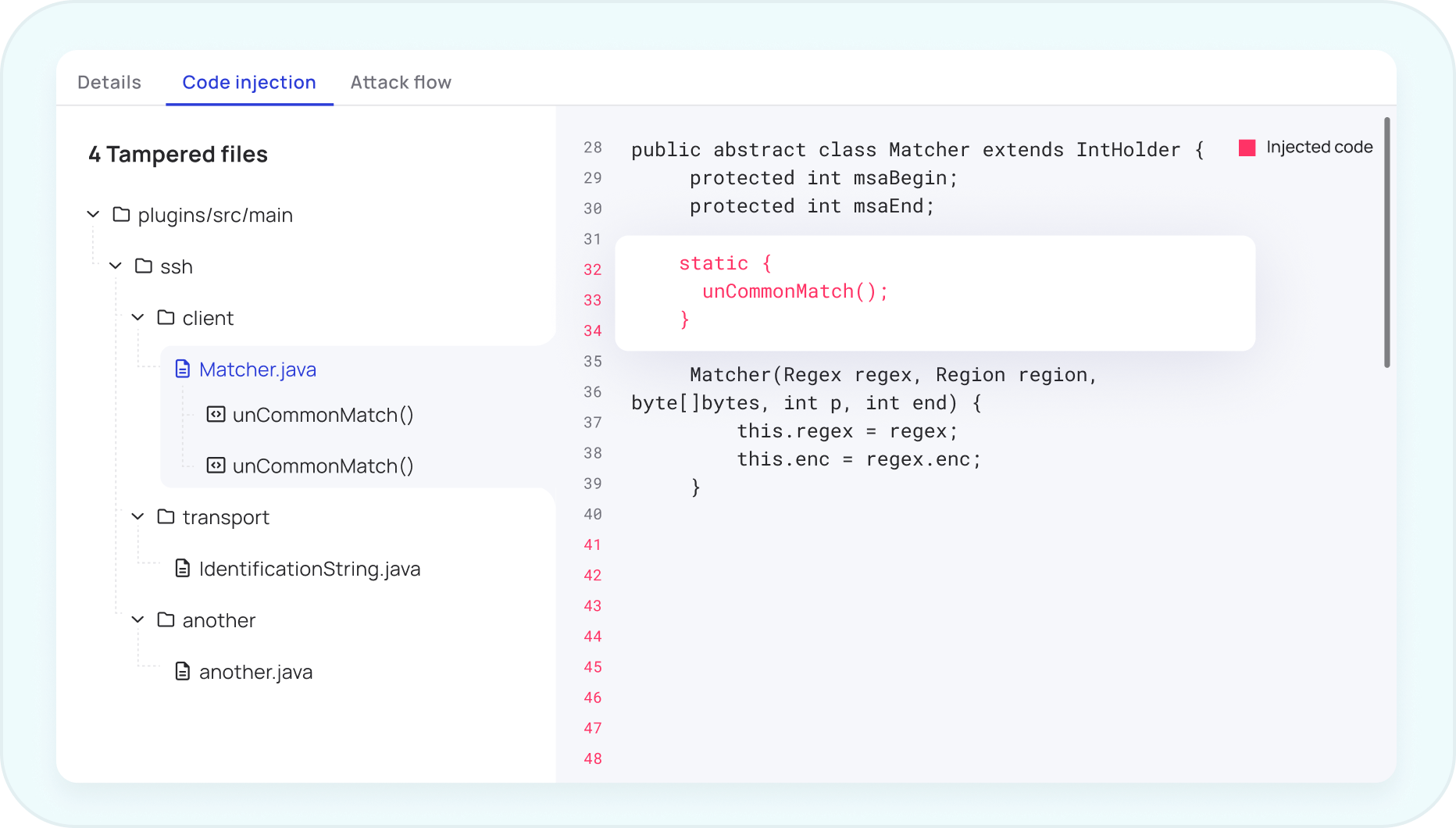
Detect SSC Attacks
Map your unknown risk surface with the only software supply chain security solution based on patent-pending Binary-to-Source technology that exposes malicious code attacks, trojans, and supply chain risks in both your open-source and custom builds during pre and post- production.
Backed by:


What Security Leaders Say About Myrror
What Security Leaders Say About Myrror
We’ve onboarded Myrror for our SOC2 purposes and to keep our SDLC secure, but we also quickly realized that their prioritization and remediation engines save us hours of triaging work, which is a game changer in open-source security.

Myrror’s approach to Open-Source security is unique. Protecting the organization from Software Supply Chain attacks while prioritizing known vulnerabilities ensures security and improves MTTR

As a Cybersecurity company, our software integrity is a top priority. Having Myrror verify each component ensures that we ship only trusted software to our customers.

Myrror helps us complete our shift-left picture, giving us visibility to our SDLC and helping us prioritize our most urgent vulnerabilities.