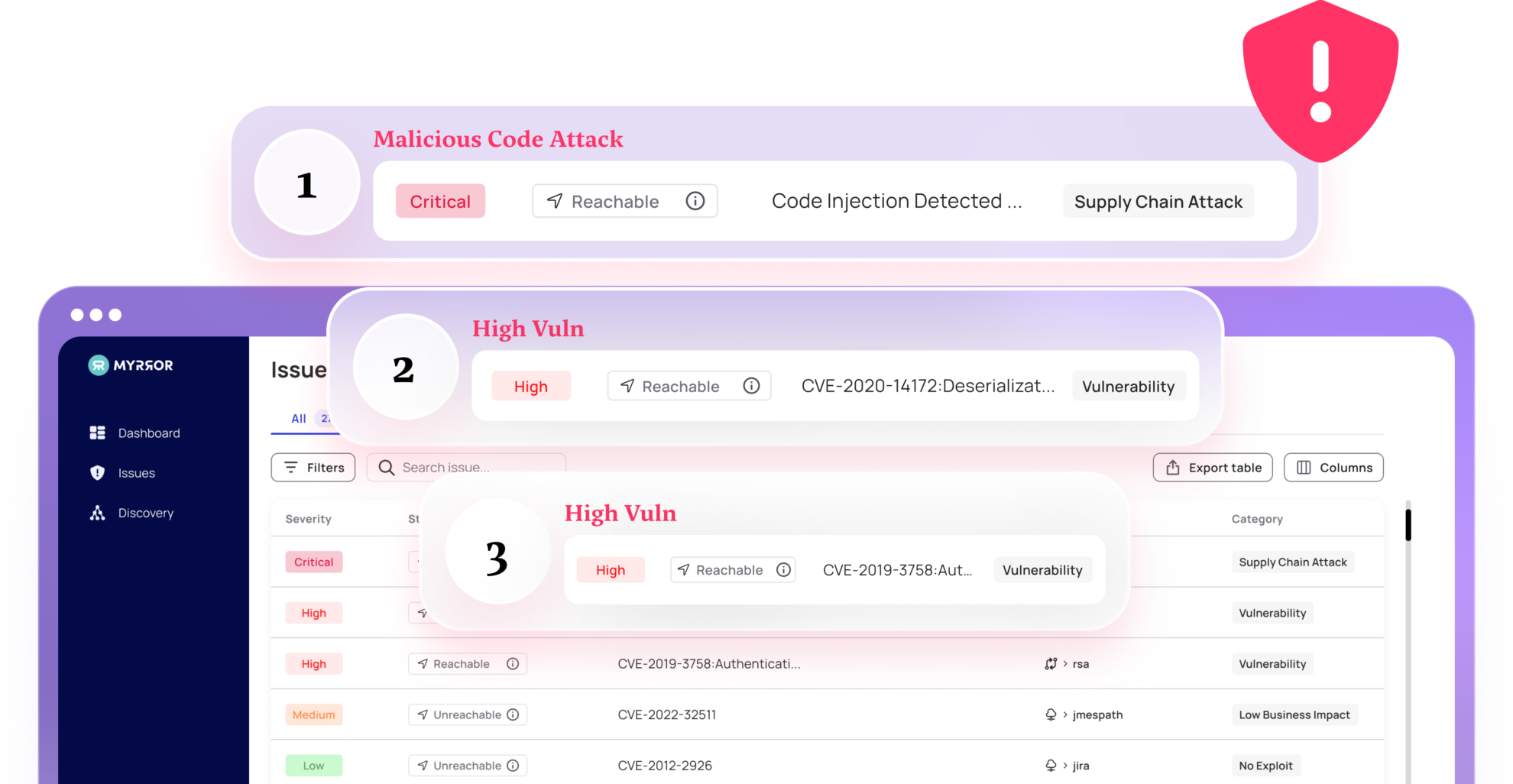
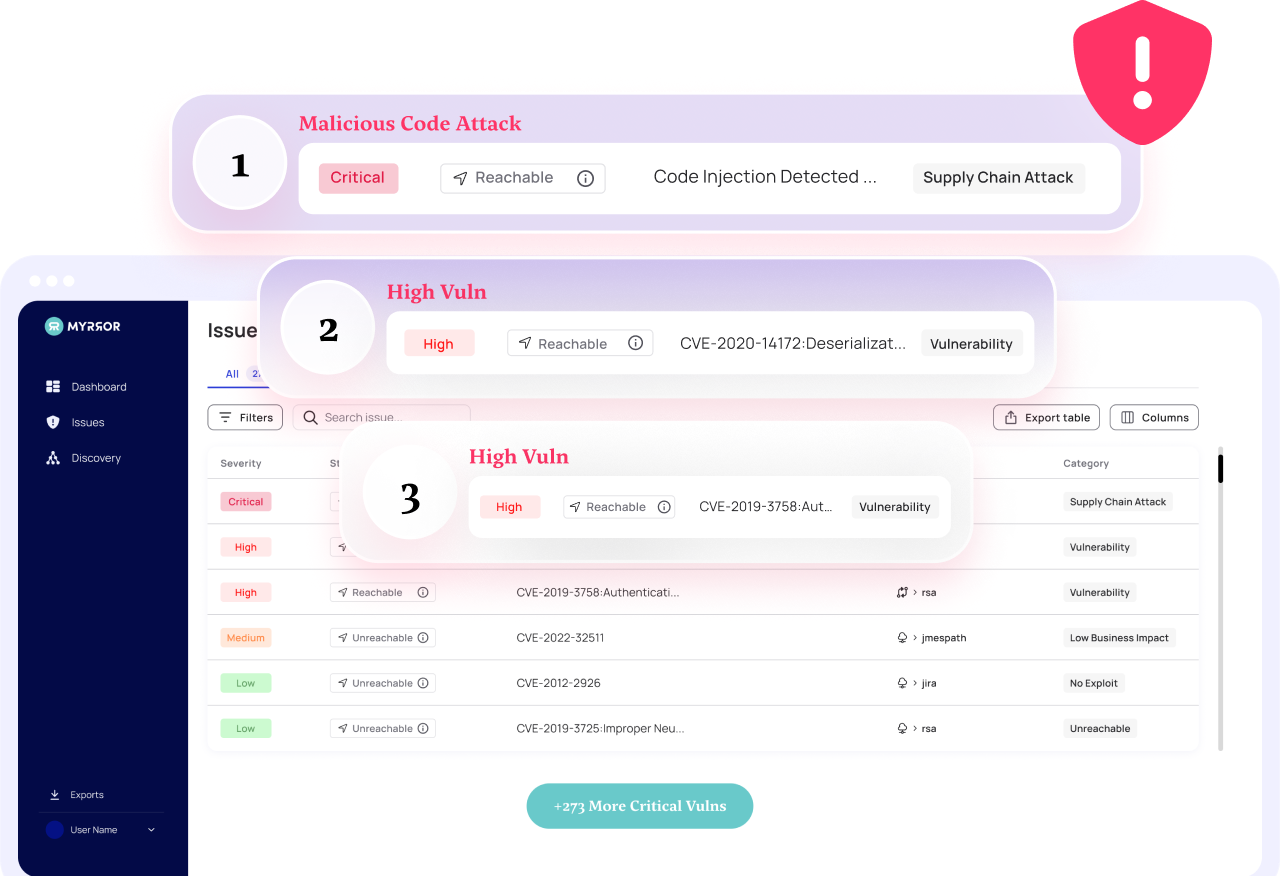
The Microsoft Threat Intelligence team suspects that the Lazarus group is behind a new attack on Cyberlink, a Taiwanese multimedia software company. Bleeping Computer reported the attack last Wednesday and details are just starting to unravel.
What we do know is that a trojanized installer was discovered on CyberLink’s update infrastructure and was found on approximately 100 devices globally. We can also state with a certain level of confidence that the attackers had the build process on their minds whilst executing the attack.
There are two most probable scenarios that I see:
- CyberLink’s build process was breached and malware was injected into an executable.
- The download server was breached and a trojanized version of the installer was added and signed using a stolen certificate.
In any case, the malicious executable was signed as legitimate software, providing additional evidence that relying on certification as a trust validation for your software is insufficient. In both cases, the core of this attack is the malware injected into CyberLink’s product that is then deployed by their customers, spreading the attacks further.
If the first scenario reminds you of the notorious SolarWinds attack, you are spot on. Although open source attacks are increasing in frequency, they are not easily detectable and by the time they are discovered it’s too late. Up until recently, there there was no salient detection solution available.
This scenario is well documented with reports alluding to a 742% increase in attacks originating in open source. If this is the case, it is reasonable to assume there is a compromised package out there that other developers are using. This package is either tampered with or confused with a legitimate one.
In any event, the compromised artifact was shipped to production releasing an infected installer for use. It is not yet clear what the attack intent or impact is, but detecting and preventing attacks from open source dependencies, and verifying builds, is essential to ensuring software integrity and passing malware to downstream customers.
Following the attack in 2020, SolarWinds attempted to address the validation challenges by employing reproducible build methods in which the same code is compiled in two different CI/CD pipelines to reach identical artifacts. However, this attempt is high-maintenance and adds a huge overhead in budget and resources to the modern engineering ecosystem, mainly due to the heavy lift of reproducing builds.
At Myrror, we have a different, simple, yet novel solution. To go back to the basics and distinguish between known risk, i.e. vulnerabilities, and unknown risk, i.e. malicious code attacks.
When looking for the unknown, it’s logical to analyze the source and the executable to ensure no unintended functionalities exist in the final artifact. As such, we have developed the technology that allows us to detect maliciously added code to the final binary as we call it Binary-to-Source Analysis. Using this method allows us to unknown attacks, like what happened in CyberLinks, 3CX, SolarWinds, and many others, to ensure code integrity.