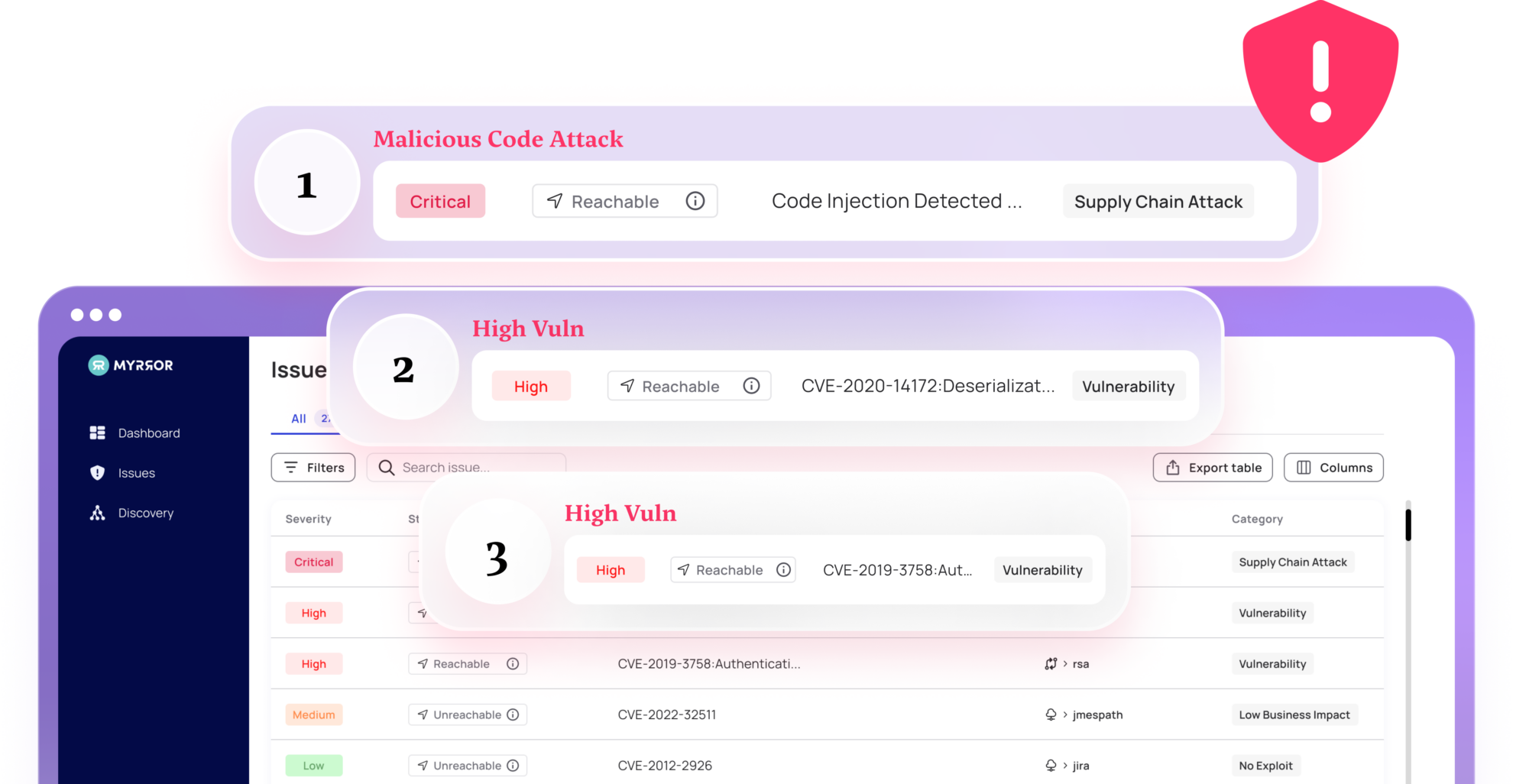
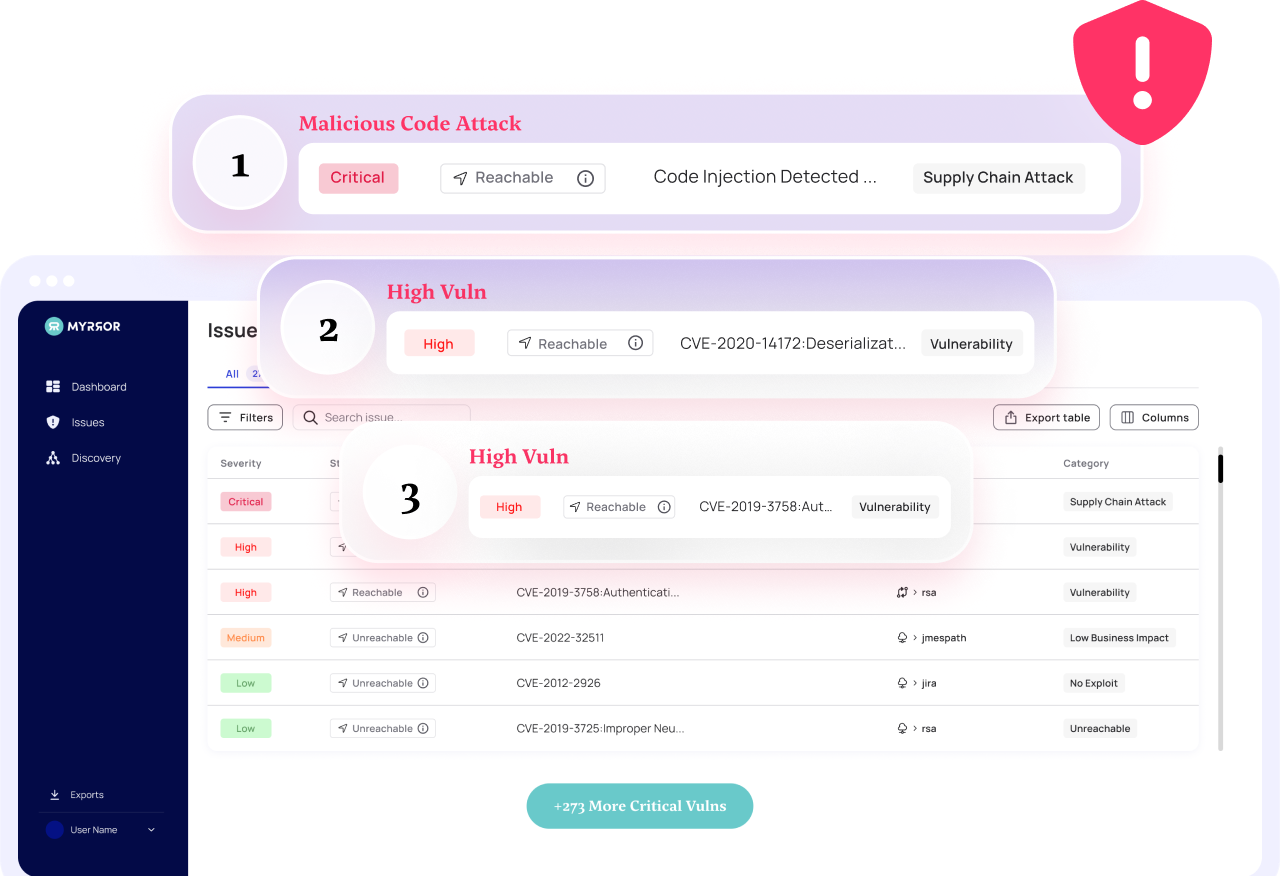
Vulnerability Detection

Myrror performs deep vulnerability checks across the entire set of your open-source dependencies, ensuring that the software you rely on to build your business – doesn’t end up destroying it.






Best-in-Class Prioritization
Myrror is, first and foremost, a new kind of Software Composition Analysis (SCA) platform.
We start by doing what SCAs have been doing for a long time: finding & prioritizing vulnerabilities. We then take this process and enrich it with our proprietary analysis capabilities:
- Reachability
- Exploitability
- Business Impact
Comprehensive Coverage
The modern supply chain landscape is comprised of numerous attack surfaces and an infinite number of potential attack vectors.
Myrror covers multiple chains in the link – detecting vulnerabilities, automating prioritization, detecting upstream supply chain attacks, and aiding the remediation process.
Deep Integrations
Myrror was built to be a team player – we work within most major CI/CD platforms, including GitHub, BitBucket, GitLab, Azure DevOps, and more.
Regardless of where your dependencies come from – or where they’re going – we’ll be there.


How It Works
Step 1
Myrror connects to your source code management system and scans all of your dependencies for vulnerabilities and supply chain attacks.
Step 2
Myrror prioritizes all of the vulnerabilities and attacks according to reachability, exploitability, and business impact.
Step 3
Myrror automatically generates a remediation plan that takes into consideration all newly introduced vulnerabilities and calculates the optimal path for fixing as many of them as possible.