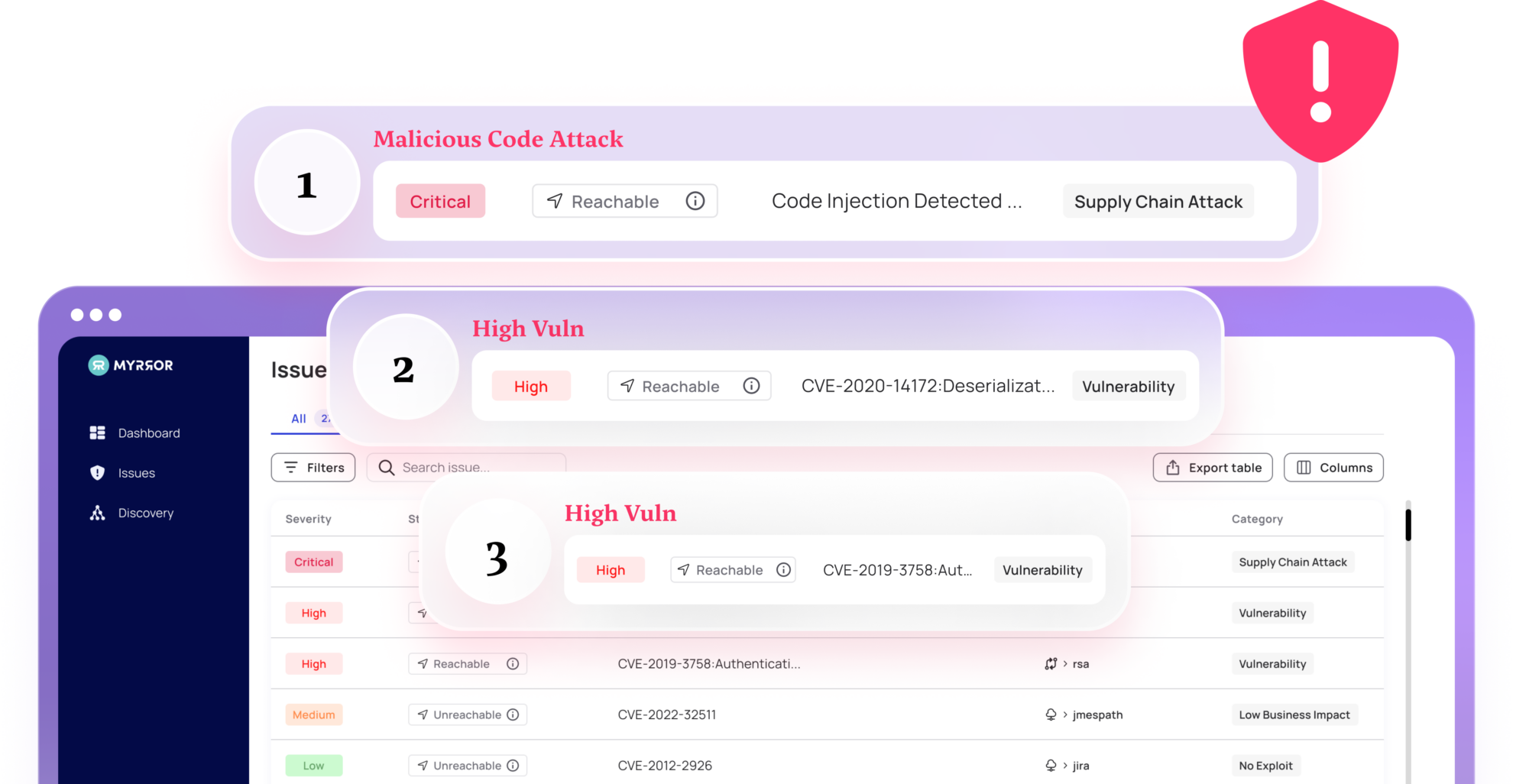
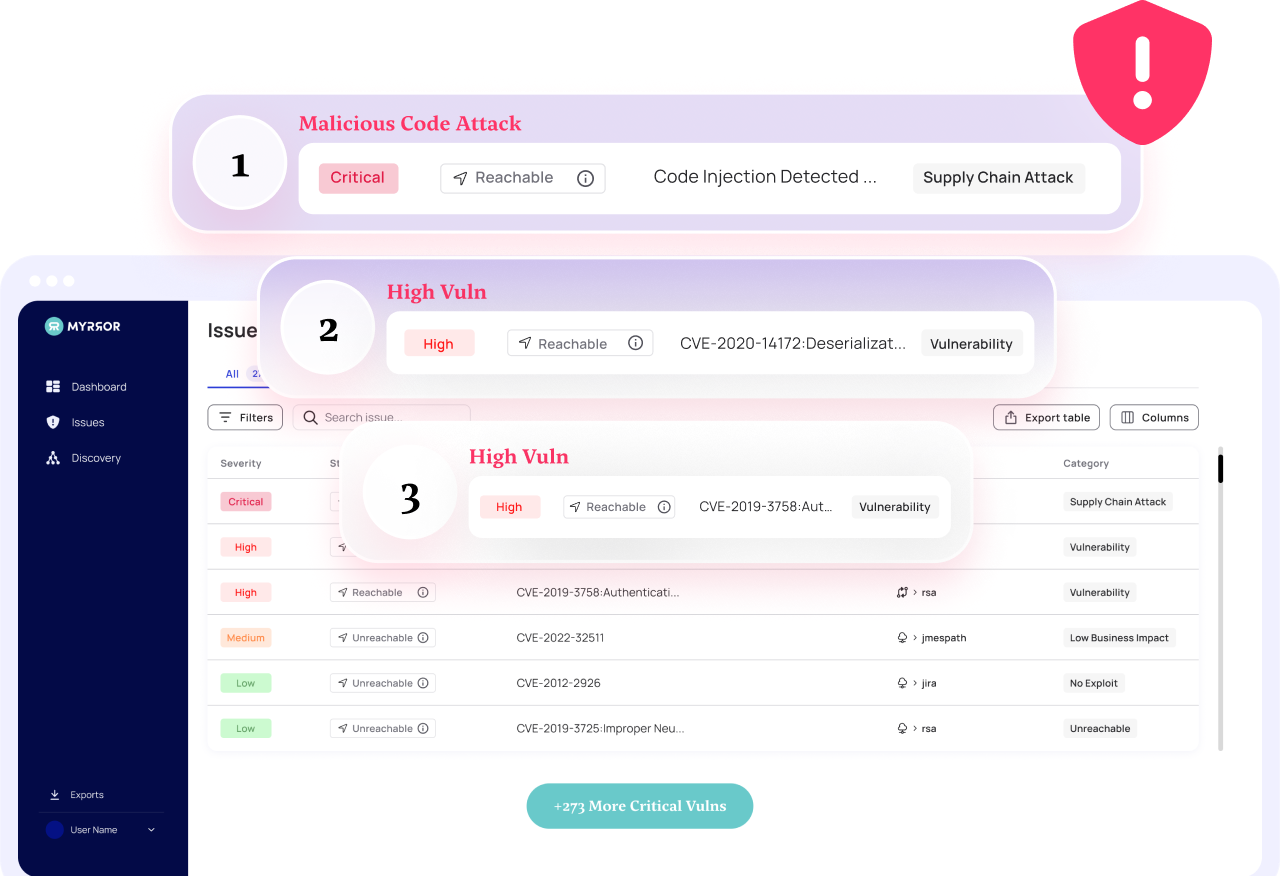
Vulnerability Prioritization

Myrror prioritizes your vulnerabilities not only based on their presence in the code but also considering their reachability and exploitability. Gain true visibility into the vulnerabilities that matter most and put an end to alert fatigue.






Reachability Analysis
Traditional SCAs read the manifest file, see if a vulnerable version of the package exists, and mark the vulnerability as a risk.
Myrror concentrates on determining if a specific piece of vulnerable code is reachable, and it only flags packages that can be reached in practice.
Myrror’s Reachability Engine analyzes both direct and transitive dependencies, creating an accurate foundation for remediation efforts.
Exploitability Analysis
Reachability indicates that the vulnerable code can be accessed in practice, but this does not necessarily imply it can be exploited.
Myrror’s proprietary analysis engine assesses whether the vulnerable code is actually exploitable and marks each vulnerability with a flag to indicate whether an exploit for it is actually available – allowing for even deeper prioritization.
Shift Left Approach
Static reachability analysis embodies a Shift Left approach, which is crucial for establishing effective security practices and detecting vulnerabilities early in the SDLC process, thereby preventing these vulnerabilities from ever reaching production.
By Doing so, Myrror reduces the risk – and associated cost – of late-stage fixes.


How It Works
Step 1
Once Myrror is connected to the SCM a discovery process begins. The process uncovers all of the organization’s dependencies.
Step 2
The vulnerability detection process begins, and surfaces up all known vulnerabilities and supply chain attack attempts across the monitored repositories.
Step 3
The Reachability Engine verifies if the package is reachable in practice, whereas the Exploitability Engine determines whether an exploit exists in the wild. Additionally, Myrror checks the availability of a fix for the issue.
Consequently, users are provided with a concise, prioritized, and actionable list of actual risks, enabling teams to concentrate on and remediate real (and relevant) threats.