Your biggest security threat might be a line of code nobody in your company wrote. In the case of the infamous vulnerability in Apache’s Log4j Java library, we saw this play out on a massive scale. Countless systems were exposed because of a single, overlooked flaw buried in a dependency on an open-source logging tool used in millions of applications worldwide.
Even two years after the log4j incident made headlines, 4000 companies remain exposed to the vulnerability Log4SHell. The nightmare of having critical vulnerabilities lurking in third-party libraries and components is real. If you’re responsible for securing applications, mapping out dependencies is crucial to keep every vulnerability in system components on your radar.
What is Application Dependency Mapping?
Application Dependency Mapping (ADM) is a process that uncovers and documents all the obvious and hidden connections that keep your applications running. Think of it as a detailed map showing the complex web of dependencies your applications rely on, such as microservices, APIs, third-party libraries, and cloud infrastructure.
Each high-profile news story about the latest software supply chain hack reinforces the dangers of unmanaged dependencies. Threat actors constantly scout for web apps that run vulnerable components. A lack of visibility can allow vulnerable third-party libraries or misconfigured APIs to slip through the cracks, putting your applications at risk of data breaches. ADM helps you proactively manage these third-party risks by allowing you to identify weak points before bad actors can exploit them.
Why is Effective Application Dependency Mapping Important?
1. Enhanced Visibility
DevSecOps teams need a clear picture of how all the moving parts of apps fit together, especially in microservices architectures where applications rely on a mishmash of APIs, libraries, and third-party services. ADM cuts through that complexity by providing a map of your dependencies, allowing you to see what’s running in production and interacting with what, and assess risk across the system.
2. Proactive Security
A reactive, patch-and-pray approach to software security simply doesn’t cut it anymore. With ADM, you can continuously monitor your application environment for shifts in dependencies and configurations, ensuring that you catch and address vulnerabilities or misconfigurations before they become significant issues. This constant monitoring strengthens your overall security posture.
3. Identifying Hidden Risks
It’s strikingly common for vulnerabilities to creep into apps through overlooked or unmanaged dependencies. Developers often bring in third-party libraries to speed up development (74% of commercial codebases contain open-source components), but these can become backdoors for attackers if not adequately monitored. ADM enables your team to detect risks within these components by flagging hard-to-detect threats from outdated or vulnerable libraries before attackers can exploit them.
4. Reduced Technical Debt
The benefits stretch beyond security because a clear map of dependencies lets you easily see redundant or obsolete components. In fast-paced DevOps environments, it’s easy to accumulate outdated or unnecessary dependencies, which, aside from potentially introducing vulnerabilities, also clog up systems. Removing these components helps your business run leaner, more secure applications.
5. Streamlined Troubleshooting
When things break, finger-pointing between development, security, and operations can waste time. With ADM, you no longer need to scramble through logs or guess where the problem lies. By giving your team a clear view of dependencies and their interactions, ADM dramatically reduces the time spent on root cause analysis. It also accelerates incident response and minimizes downtime, a critical advantage in environments that demand constant uptime and rapid releases.
The Four Methods of Application Dependency Mapping
1. Sweep and Poll
This method works by scanning your environment regularly to collect information on running applications and their connections. The sweep and poll approach typically uses API calls, system logs, or direct queries to gather data from network devices, servers, or cloud platforms.
These scans—often scheduled or triggered manually—look for configuration files, open ports, and active connections. You can then use them to build a picture of your application dependencies. This lightweight approach doesn’t require installing software agents on servers.
Since the scans are periodic, you only get snapshots of your environment at specific points in time, which means you can miss changes between scans. This creates blind spots that could lead to security gaps or performance issues if not caught in time.
2. Network Monitoring
Network monitoring captures application dependencies by observing the traffic flowing between systems. This method involves using packet sniffers or flow analysis tools to monitor how data moves through the network, allowing you to map out which applications are communicating and how often. By analyzing network traffic patterns, security and operations teams can infer dependencies between services, applications, and infrastructure components.
This network monitoring method provides a detailed, real-time view of interactions. It helps find anomalies or unauthorized communications that might not be visible through other approaches. However, it generates large amounts of data that require filtering and correlation to map out dependencies correctly.
3. Agent on Server
With Agent on Server, you install a lightweight software agent directly on each server to gather detailed info about its applications and services. The software agent collects data such as process activity, open ports, system calls, and service interactions, which you can then use to map out application dependencies.
Agents can track interactions and provide deeper insights into resource usage, configuration changes, and performance metrics. Installing and managing agents on each server introduces overheads, though, both in terms of system resources and operational complexity. Agents need to be maintained, updated and monitored.
4. Automated ADDM
Automated Application Dependency Discovery and Mapping (ADDM) is an advanced, automated approach to mapping dependencies across applications and infrastructure. ADDM tools use a combination of the above methods, with a sprinkling of other advanced features like machine learning for anomaly detection, change tracking, and real-time alerting.
These solutions also allow data aggregation from multiple sources, such as configuration management databases and service management tools, to build a dynamic, real-time map of all dependencies.
4 Steps to Perform Effective Application Dependency Mapping
1. Identify Data Sources
To start, identify what information to gather from a broad range of systems and tools to capture the complete picture of your application dependencies. Diverse data sources drive more comprehensive visibility of app dependencies.
Consider the following:
- Logs from systems like Syslog, Windows Event Viewer, and Journald help identify dependencies between servers and the services they host.
- Examining CI/CD pipeline outputs to reveal where third-party libraries and APIs are integrated into your build and deployment.
- API calls to understand dependencies in microservice architectures or third-party SaaS integrations.
- Scan your code repositories (e.g., GitHub, Bitbucket) with SBOM tools to identify third-party components and libraries.
2. Create an Inventory of Apps and Services
Once you’ve identified the data sources to build a dependency map, create an initial inventory of all your applications, services, and infrastructure components (if you don’t already have this inventory). This list should include web app servers, databases, APIs, microservices, container images, and third-party integrations. Gathering this baseline information is essential to leaving no stone unturned when building a dependency map.
Start by discovering all running applications in your environment, manually or using automated tools. You can leverage built-in discovery services to capture running cloud-native apps in cloud environments. Tools like Kubernetes’ kubectl command and Rancher provide insights into which containers are running, what services they are exposing, and how they interact. Orchestration platforms like Docker Swarm or Kubernetes also track the relationships between containers and infrastructure.
Check API usage logs and track external libraries using your package managers. Remember to include all traditional and cloud-based databases in your inventory.
3. Build a Map
After establishing an inventory, it’s time to run the first mapping scan and build a baseline map of your application dependencies. This step aims to visualize how all the components you’ve inventoried are connected and pinpoint which services depend on others.
Ensure that your map includes service-to-service interactions and other critical dependencies such as storage (e.g., S3 buckets, databases), external APIs, and third-party components. Visualization tools can help create a graphical representation of your application dependencies. Some ADM solutions will have built-in capabilities for visualizations.
Validate this initial map against your inventory and logs to ensure accuracy. Cross-check the dependencies identified by your tool against your manual inventory and service logs. Look for missing services, overlooked APIs, or external components that might have been missed during the initial mapping.
4. Continuously Monitor and Update
Applications and dependencies evolve rapidly, especially in dynamic environments driven by microservices, cloud-native architectures, and CI/CD pipelines. Ideally, you want to track new services, API calls, infrastructure changes, and third-party integrations in real-time. Continuous monitoring ensures that as new services are added or existing services are updated, your map remains reflective of the current state of your app environment.
Remember that many dependencies stem from configuration changes, especially in cloud or virtualized environments. Use infrastructure-as-code (IaC) tools like AWS CloudFormation to track these configuration changes and update your map accordingly.
Expose Hidden Risks, Secure Your Stack
Application dependency mapping (ADM) is far more than mapping connections—it’s about exposing hidden risks before they become full-blown threats. ADM helps you gain a deep understanding of how every component interacts within your infrastructure.
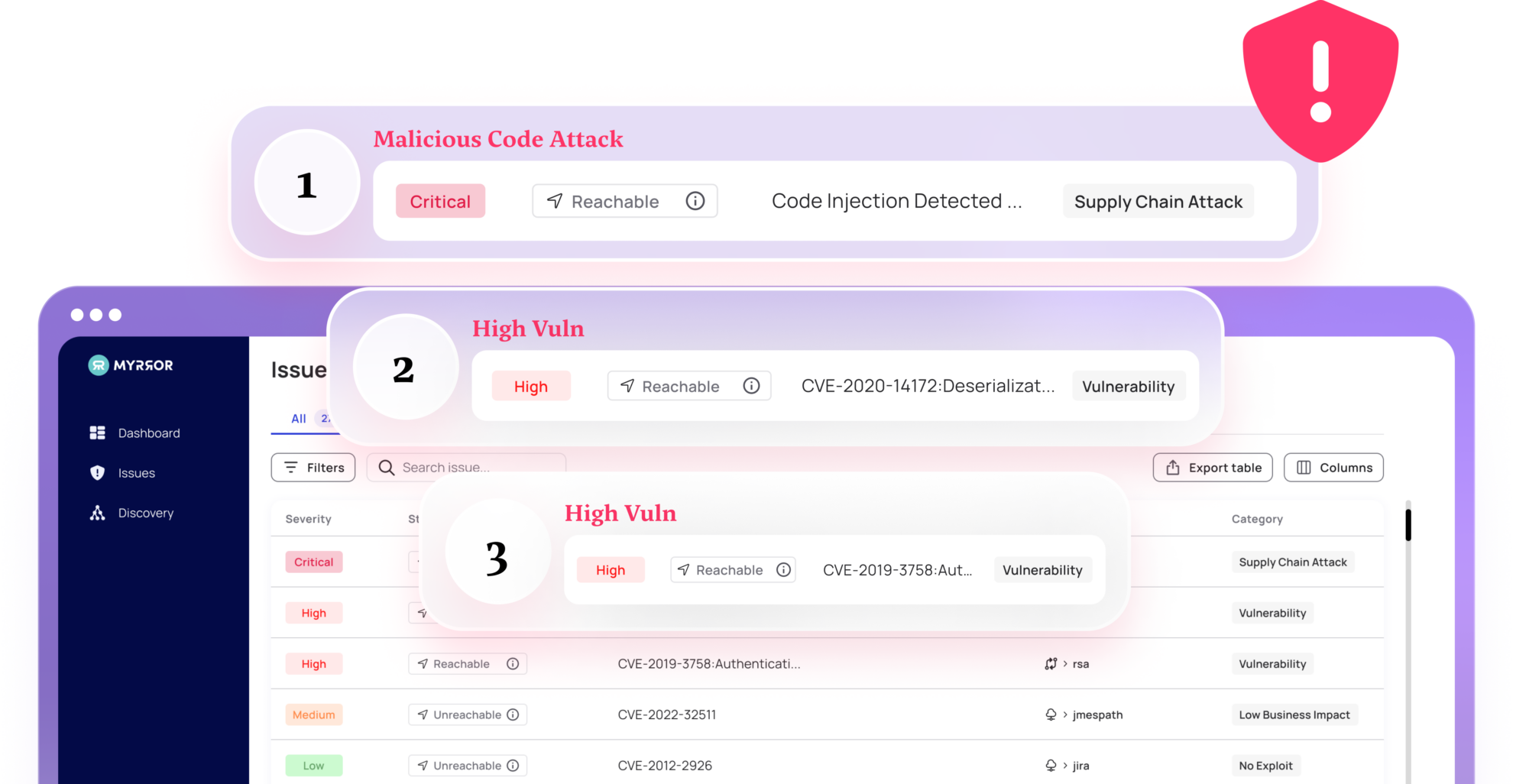
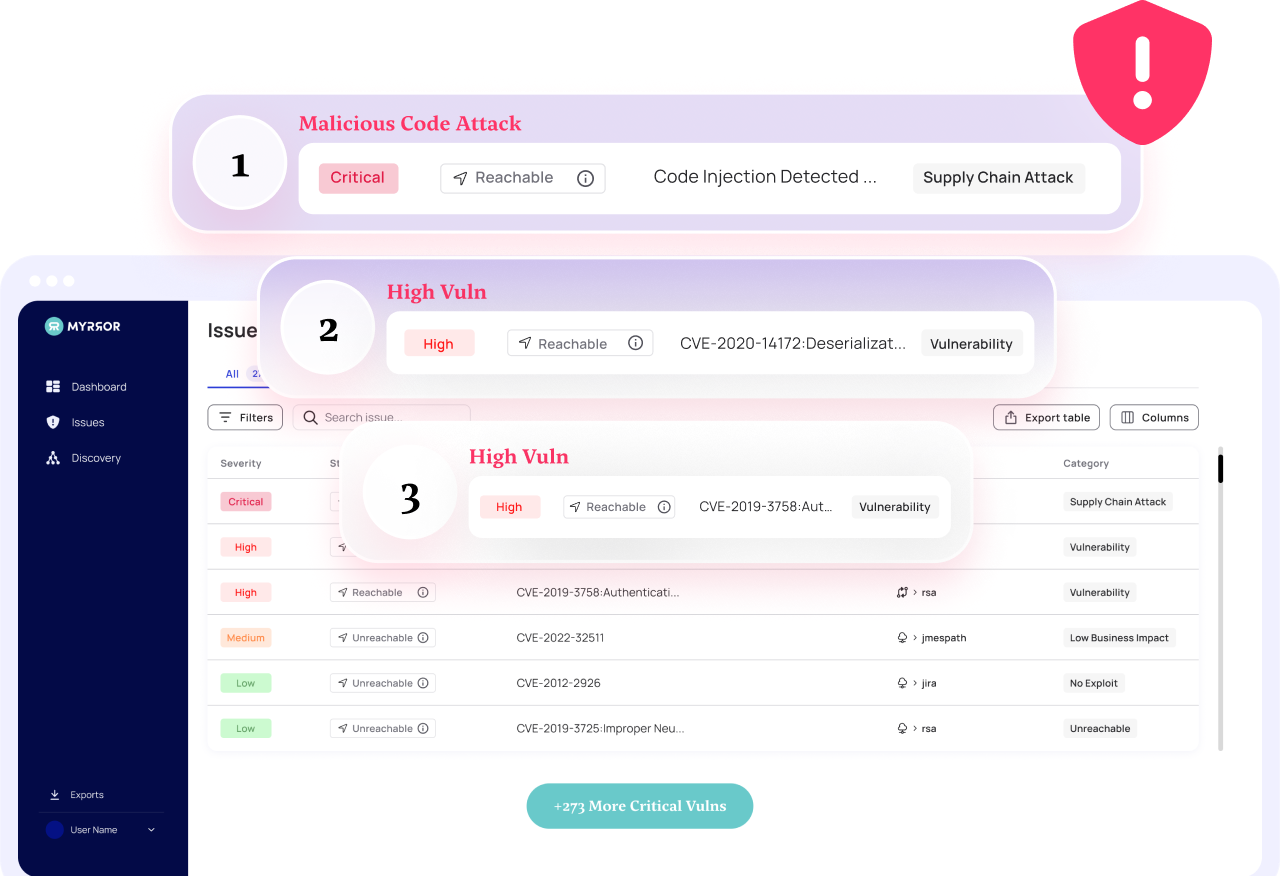
With Myrror Security, application dependency mapping becomes effortless. This supply chain security platform integrates seamlessly into DevSecOps workflows and generates an SBOM tailored to your application. Myrror scans deeply across your open-source dependencies and identifies weaknesses and vulnerabilities. A unique binary-to-source AI engine can even detect supply chain attacks from malicious open-source packages that traditional vulnerability scanners miss. Learn more here.